According to a study, 60% of web applications are vulnerable to cross-site scripting attacks. In fact, 30% of all web application attacks use cross-site scripting. Not only that, cross-site scripting flaws are also considered a critical threat to your web application security by OWASP.
Despite this, very few businesses take cross-site scripting attacks seriously, let alone do something to protect themselves. If you want to know more about cross-site scripting attacks, this article is for you. In this article, we will discuss the various aspects of cross-site scripting attacks, including how they work, their types, how to prevent them, and how to mitigate their effects.
- Cross Site Scripting: Everything You Need To Know
- What is Cross Site Scripting?
- How does Cross Site Scripting work?
- What are the Types of Cross Site Scripting Attacks?
- 1. Reflected Cross Site Scripting
- 2. Stored Cross Site Scripting
- 3. DOM-based Cross Site Scripting
- How to prevent Cross Site Scripting attacks?
- 1. Input validation:
- 2. Output encoding:
- 3. HTTP-only cookies:
- How to mitigate the effects of Cross Site Scripting attacks?
- 1. Disable the affected page:
- 2. Remove the malicious code:
- 3. Notify affected users:
- 4. Implement a web application firewall:
- 5. Implement a content security policy (CSP):
- 6. Regularly scan for vulnerabilities:
Cross Site Scripting: Everything You Need To Know
What is Cross Site Scripting?
Cross-site scripting, or XSS, is a type of security vulnerability that affects web applications. XSS attacks allow an attacker to inject malicious code, such as scripts or HTML, into a website viewed by unsuspecting users. The consequences of such an attack can be severe, including the theft of sensitive user data, hijacking of user sessions, and even complete compromise of the entire web application.
How does Cross Site Scripting work?
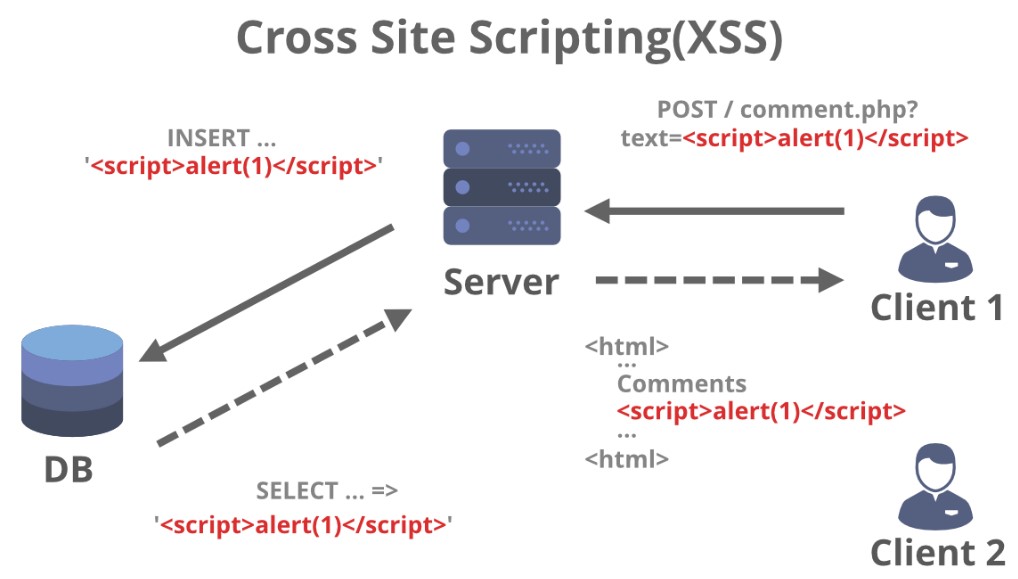
Cross-site scripting attacks work by exploiting the trust that web applications have in user input. Web applications rely on user input, such as form submissions or search queries, to generate dynamic content. When a user submits input to a web application, the application typically processes that input and generates a response.
An attacker can exploit this process by injecting malicious code into the user input. For instance, an attacker could inject a script that steals the user’s cookies, allowing the attacker to hijack the user’s session.
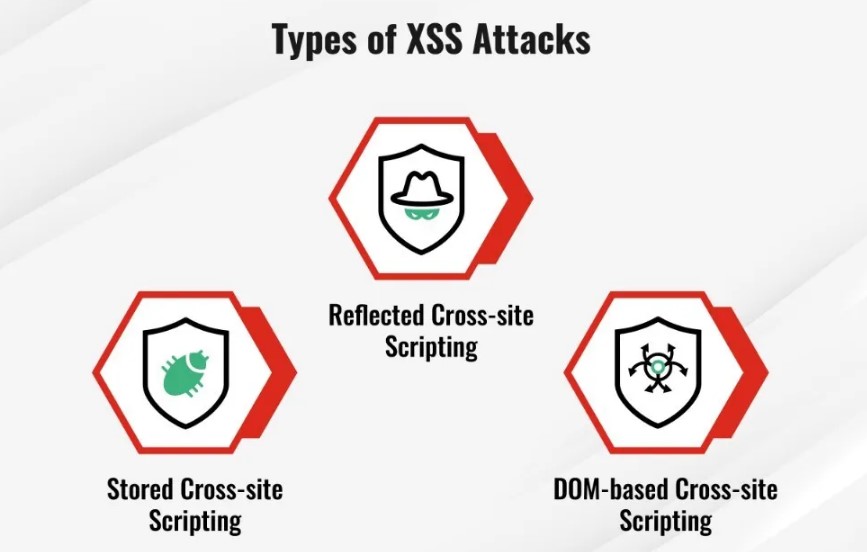
What are the Types of Cross Site Scripting Attacks?
There are three main types of Cross Site Scripting attacks: reflected, stored, and DOM-based.
1. Reflected Cross Site Scripting
Reflected Cross-Site Scripting attacks occur when an attacker injects malicious code into a web application that is then reflected back to the user. For instance, an attacker might craft a phishing email that includes a link to a website that includes a reflected Cross-Site Scripting attack. When the user clicks the link, the malicious code is executed, allowing the attacker to steal user data or hijack user sessions.
2. Stored Cross Site Scripting
Stored Cross-Site Scripting attacks occur when an attacker injects malicious code into a web application that is then stored on the server. The malicious code is then served to all users who visit the affected page. For instance, an attacker might inject a script into the comment section of a blog post. When other users view the blog post, the script is executed, allowing the attacker to steal user data or hijack user sessions.
3. DOM-based Cross Site Scripting
DOM-based Cross-Site Scripting attacks occur when an attacker injects malicious code into a web application that is then executed by the user’s web browser. These attacks are particularly difficult to detect and prevent, as the malicious code is not transmitted to the server. Instead, the attacker relies on the web application to execute the code directly.
How to prevent Cross Site Scripting attacks?
Preventing XSS attacks requires a multi-layered approach that includes both server-side and client-side defenses. Here are some common techniques that can be used to prevent these attacks:
1. Input validation:
The first line of defense against XSS attacks is input validation. Web applications should validate all user input, such as form submissions and search queries, to ensure that it does not contain any malicious code.
2. Output encoding:
Web applications should encode all output to ensure that any user-generated content is displayed as plain text, rather than as executable code.
Content security policy (CSP): A CSP is a security mechanism that allows web administrators to specify which resources a browser should be allowed to load on a web page. By limiting the resources that a browser can load, administrators can prevent malicious scripts from being executed.

3. HTTP-only cookies:
HTTP-only cookies are a type of cookie that can only be accessed by the server, rather than by client-side scripts. By using HTTP-only cookies, administrators can prevent attackers from stealing user cookies through Cross Site Scripting attacks.
How to mitigate the effects of Cross Site Scripting attacks?
Even with the best prevention techniques, Cross-Site Scripting attacks can still occur. When a Cross-Site Scripting attack is detected, there are several steps that can be taken to mitigate its effects:
1. Disable the affected page:
The first step is to disable the affected page to prevent further damage from occurring.
2. Remove the malicious code:
Once the affected page has been disabled, the malicious code should be removed from the server.
3. Notify affected users:
If user data has been compromised, it is important to notify affected users and advise them to change their passwords or take other appropriate action to protect themselves.
4. Implement a web application firewall:
A web application firewall (WAF) can be used to detect and block Cross-Site Scripting attacks before they reach the web application. A WAF can also be configured to block any suspicious traffic or requests.

5. Implement a content security policy (CSP):
A CSP is a security mechanism that allows web administrators to specify which resources a browser should be allowed to load on a web page. By limiting the resources that a browser can load, administrators can prevent malicious scripts from being executed.
6. Regularly scan for vulnerabilities:
Regularly scanning for vulnerabilities and conducting security assessments can help identify potential Cross-Site Scripting vulnerabilities and prevent attacks from occurring in the first place.
Even though preventing cross-site scripting attacks should be your top priority, having a plan in place to mitigate the effects of an attack is equally important. By implementing a combination of prevention techniques and mitigation strategies, web administrators can better protect their users and minimize the impact of any potential Cross-site scripting attacks.
Did this article help you in understanding cross site scripting attacks? Share your feedback with us in the comments section below.





Add comment