In the fast-paced world of business, where digital communication reigns supreme, a subtle and cunning threat lurks in the shadows: Business Email Compromise (BEC). Imagine a scenario where trusted emails turn treacherous, and cyber criminals exploit the very essence of communication to infiltrate organizations and orchestrate financial fraud. This captivating guide delves deep into the realm of BEC, revealing its sinister techniques and providing business owners with the knowledge they need to safeguard their enterprises from this ever-evolving menace.
Picture this: a seemingly innocuous email, camouflaged as a legitimate request from a respected colleague or trusted business partner. Unbeknownst to the recipient, it harbors dangerous intent, ready to manipulate human vulnerabilities and exploit blind trust. In this guide, we unravel the secrets of BEC, empowering business owners with the insights and strategies necessary to thwart these stealthy attacks.
From dissecting the devious tactics employed by cybercriminals to understanding the anatomy of a successful BEC attack, we leave no stone unturned. Discover how these fraudsters meticulously research their victims, expertly impersonating executives and suppliers with chilling accuracy.
Business Email Compromise: Everything You Need To Know
What is Business Email Compromise (BEC)?
Business Email Compromise (BEC) is a type of cyber attack that targets businesses and organizations. BEC attacks involve the use of fraudulent emails, often mimicking the email address of a trusted party, such as a supplier or senior executive, to convince employees to transfer funds or sensitive information.
BEC attacks can take many forms, including fake invoice requests, executive impersonations, and requests for confidential information.
How Does Business Email Compromise Work?
Within the realm of cyber threats, Business Email Compromise (BEC) stands out as a particularly insidious and successful tactic. This sophisticated attack technique begins with a seemingly innocuous phishing email, meticulously designed to masquerade as trustworthy communication. Leveraging urgency and psychological manipulation, attackers employ social engineering tactics to deceive recipients into unwittingly aiding their malicious objectives. By exploiting human vulnerabilities, particularly trust and authority, BEC attacks prey on the inherent inclination of employees to comply with seemingly legitimate requests from trusted parties.
The initial phase of a business email compromise attack centers around a phishing email that convincingly mimics a reputable source. These deceptive messages often appear urgent and may masquerade as invoices from suppliers or urgent requests from high-ranking executives.

Once the recipient takes the bait and responds, the attacker skillfully employs social engineering techniques to escalate the attack, aiming to extract sensitive information or convince the victim to initiate a wire transfer. The success of BEC attacks lies in their ability to manipulate human behavior and exploit the implicit trust placed in senior executives and business partners, thus increasing the likelihood of compliance.
How Attackers Launch BEC Attacks?
1. Spoofing:
Spoofing techniques have become a go-to tool for attackers seeking to deceive their targets. By manipulating email attributes, such as the display name or sender address, attackers can make emails appear to originate from trusted sources like high-ranking executives or reputable vendors. This technique lures recipients into a false sense of security, as the email seems to come from within their own organization. Spoofing adds a dangerous layer of authenticity to malicious emails, making it imperative for cybersecurity professionals to stay vigilant and employ robust email security measures.
2. Social Engineering:
The art of social engineering lies at the heart of many successful cyber attacks, including Business Email Compromise (BEC). Attackers invest time and effort in conducting meticulous research on their target company or individuals within it. The email could contain a malicious link or a malware laden attachment.
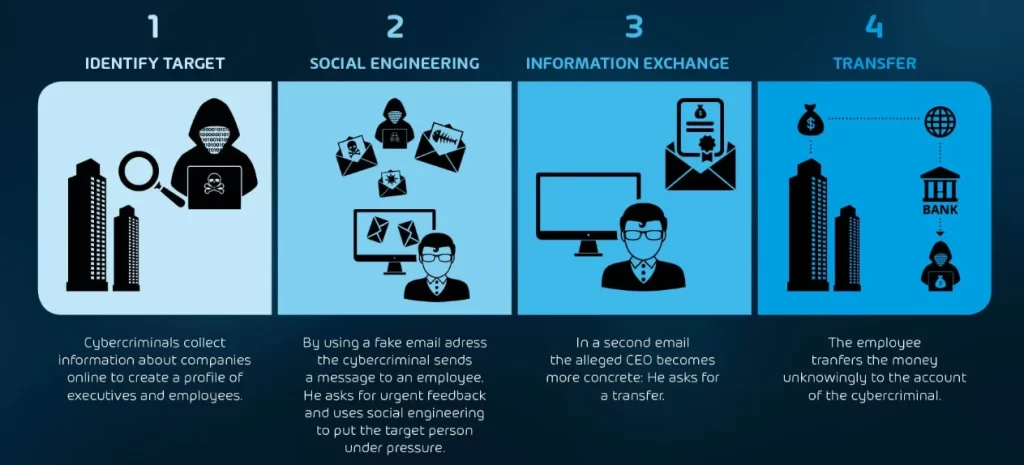
By leveraging readily available online resources, such as social media platforms and public records, attackers gain insights into the company’s hierarchy, communication patterns, and key individuals. This enables them to craft sophisticated impersonations, masquerading as executives or trusted vendors and increasing the likelihood of successful compromise.
3. Compromising Email Accounts:
Attackers may gain access to a company email account through hacking or phishing, allowing them to send fraudulent emails from a legitimate email address.
Tactics Attackers Use After Gaining Access
1. Changing Payment Instructions:
Attackers may intercept legitimate emails between the target company and their vendors, and then modify the payment instructions to direct funds to a fraudulent account.
2. Requesting Sensitive Information:
Attackers may request sensitive information, such as employee records or financial information, under the guise of conducting a legitimate business transaction.
3. Gift Card Scams:
Attackers may request that the target company purchase gift cards or other prepaid cards, and then send the codes to the attacker.
4. Payroll Scams:
Attackers may request that the target company update employee payroll information or provide access to the company’s payroll system, allowing the attacker to divert funds to a fraudulent account.
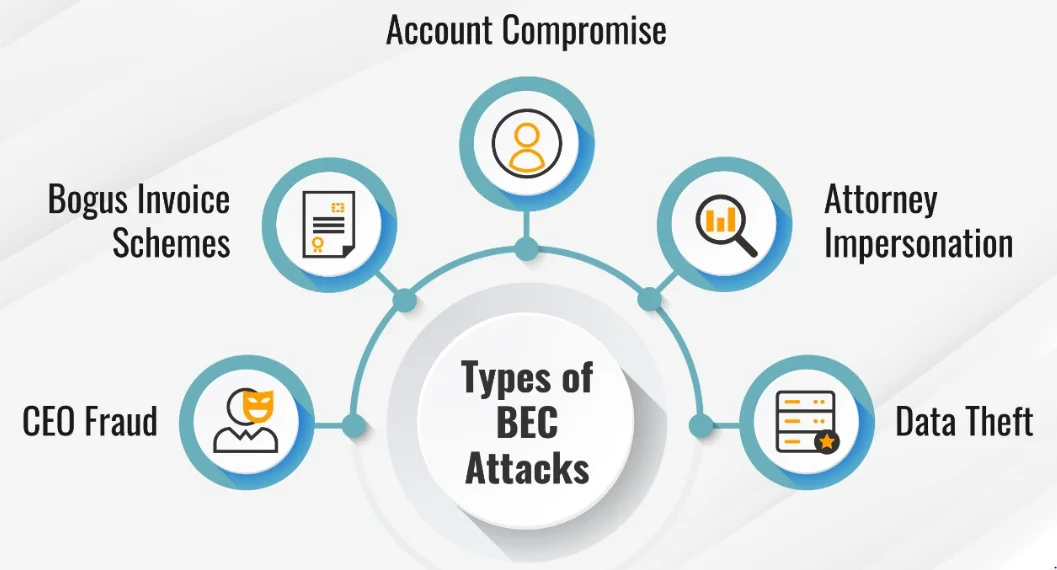
Tools to Protect Against BEC Attacks:
1. Email Filters:
Email filters are crucial in combating phishing emails and malicious attachments, acting as the first line of defense. These robust tools, commonly offered by email service providers, enable organizations to customize filters to block fraudulent or suspicious emails. Leveraging email filters empowers cybersecurity professionals to greatly diminish the risk of successful phishing attacks and minimize the impact of harmful attachments.
2. Encryption:
The digital age demands heightened protection for sensitive information, and encryption emerges as a pivotal solution. Encryption offers protection to your financial data, personal information, and other confidential content from unauthorized access.
3. Vendor Verification:
Verifying the identities of vendors and suppliers before conducting business with them can help prevent BEC attacks. This can be done through a thorough vetting process that includes verifying their contact information and checking their online reputation.





Add comment