The CISA Top Routinely Exploited Vulnerabilities report is a collaborative effort involving international partners from Australia, Canada, New Zealand, and the UK. It identifies common vulnerabilities and exposures (CVEs) that were frequently exploited by threat actors, along with their associated common weaknesses and enumerations (CWEs).
This report is essential for organizations seeking to enhance their cybersecurity defenses. In addition to listing specific vulnerabilities, the report also offers valuable recommendations for mitigating the risk of malicious attacks. These recommendations encompass a wide range of best practices and strategies to safeguard against cyber threats.
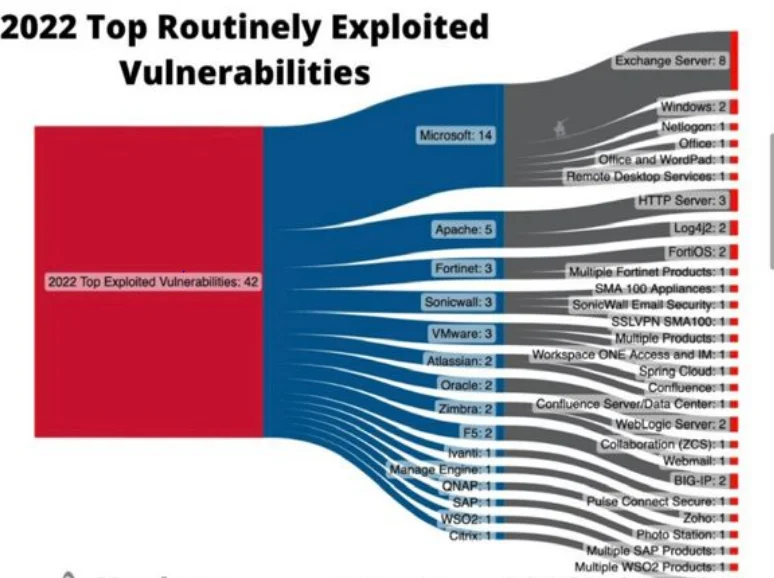
Furthermore, there is an informative visualization created by Patrick Garrity of Nucleus Security that presents the top 42 vulnerabilities from the report. This visualization provides an overview of these vulnerabilities across various vendors and their associated products. It serves as a useful tool for organizations to understand
In this article, you will learn about seven key findings from CISA’s Most routinely exploited vulnerabilities report.
7 Key Findings From CISA’s Top Routinely Exploited Vulnerabilities Report
1. Pervasive Exploitation of Legacy Systems
One of the recurring themes in CISA’s report is the persistent exploitation of legacy systems. Legacy systems are older computer systems, software, or technologies that are still in use despite being outdated and potentially vulnerable. Attackers often target these systems because they are less likely to have the latest security updates and patches. According to CISA, several vulnerabilities in legacy systems remained highly exploited. Organizations are urged to prioritize modernization efforts and invest in upgrading or replacing aging infrastructure to mitigate these cybersecurity risks effectively.
2. Continued Prevalence of Known Vulnerabilities
Surprisingly, many of the vulnerabilities routinely exploited in 2022 were well-known issues that had been previously reported and had patches available. This finding underscores the importance of timely patching and vulnerability management.
Organizations that neglect to apply patches or updates are essentially leaving their doors wide open to cybercriminals. CISA’s report emphasizes the need for proactive vulnerability scanning, patch management processes, and security awareness training for employees to reduce exposure to known vulnerabilities.
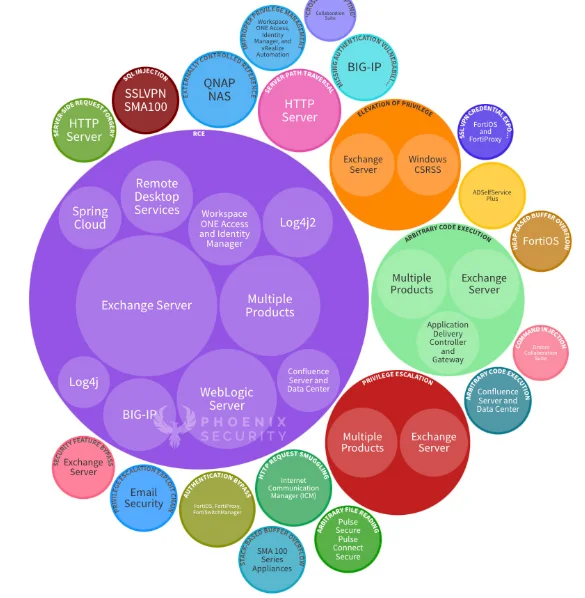
3. Attackers Favor Credential Theft
Credential theft remains a favored technique among cybercriminals. Gaining access to user usernames and passwords allows attackers to move laterally within an organization’s network and escalate privileges. The report highlights the continued use of techniques like phishing, password spraying, and credential stuffing to compromise user accounts. To counter this threat, organizations must prioritize multi-factor authentication (MFA), strong password policies, and robust user awareness training to mitigate the risks associated with credential theft.
4. Supply Chain Attacks on the Rise
CISA’s report also draws attention to the increasing prevalence of supply chain attacks. These attacks involve compromising software or hardware providers to infiltrate the target organization. High-profile data breaches like the SolarWinds have demonstrated the potential impact of supply chain attacks on both public and private sectors. Organizations are advised to scrutinize their third-party vendors and suppliers, conduct security assessments, and establish strict controls to mitigate the risks posed by supply chain vulnerabilities.

5. Heightened Risks to Critical Infrastructure
Critical infrastructure and industries such as energy, water, and transportation are prime targets for cyberattacks. CISA’s report highlights the ongoing threats to these sectors, emphasizing the need for enhanced security measures. The adoption of the Cybersecurity and Infrastructure Security Agency Act (CISA Act) in the United States underscores the importance of securing critical infrastructure. Organizations within these sectors should prioritize the implementation of robust cybersecurity frameworks, threat detection systems, and incident response plans to safeguard vital services from potential disruptions.
6. Emphasis on Security Patching and Timely Updates
Lastly, the report underscores the importance of security patching and timely updates. Many of the vulnerabilities that continue to be exploited could have been prevented if organizations had applied available patches promptly. Delayed patching not only increases an organization’s exposure to threats but also demonstrates a lack of commitment to cybersecurity best practices. Organizations must establish a comprehensive patch management program that includes regular vulnerability assessments, testing, and deployment of patches to protect their systems and networks.
7. Exploitation of Internet-Accessible Systems
Another alarming trend highlighted in the report is the exploitation of internet-accessible systems. Cybercriminals frequently target systems and services that are accessible via the internet, including remote desktop protocol (RDP) servers, virtual private networks (VPNs), and web servers.
The shift towards remote work during the COVID-19 pandemic increased the attack surface, making it even more critical for organizations to secure their internet-facing assets. Properly configuring and serv, implementing strong access controls, and regularly reviewing and updating firewall rules are essential steps to bolster cybersecurity.
Conclusion
CISA’s Top Routinely Exploited Vulnerabilities Report provides critical insights into the evolving landscape of cybersecurity threats. From the persistent targeting of legacy systems to the growing risks posed by supply chain attacks, the report highlights the need for organizations to remain vigilant and proactive in their cybersecurity efforts. By addressing these key findings, organizations can take significant steps
What did you learn from CISA’s top routinely exploited vulnerabilities report? Share it with us in the comments section below.





Add comment