Malware as a Service (MaaS) is a term used to describe the provision of malicious software over the internet for the purpose of compromising computer systems and networks. This type of service is provided by cybercriminals who sell malware-based tools and services to other malicious actors who lack the technical expertise or resources to develop their own.
What is Malware as a Service?
Malware as a Service (MaaS) is basically a service model used to deliver malware by a malware service provider such as cyber attackers and hackers. Cybercriminals offer these services to other threat actors who lack the technical expertise or resources to develop their own malware.

Types of Malware as a Service?
There are five common types of malware as service offerings.
- Ransomware-as-a-Service (RaaS)
- Banking Trojan-as-a-Service (BTaaS)
- Remote Access Trojan-as-a-Service (RATaaS)
- Exploit as a service
- Distributed Denial of Service
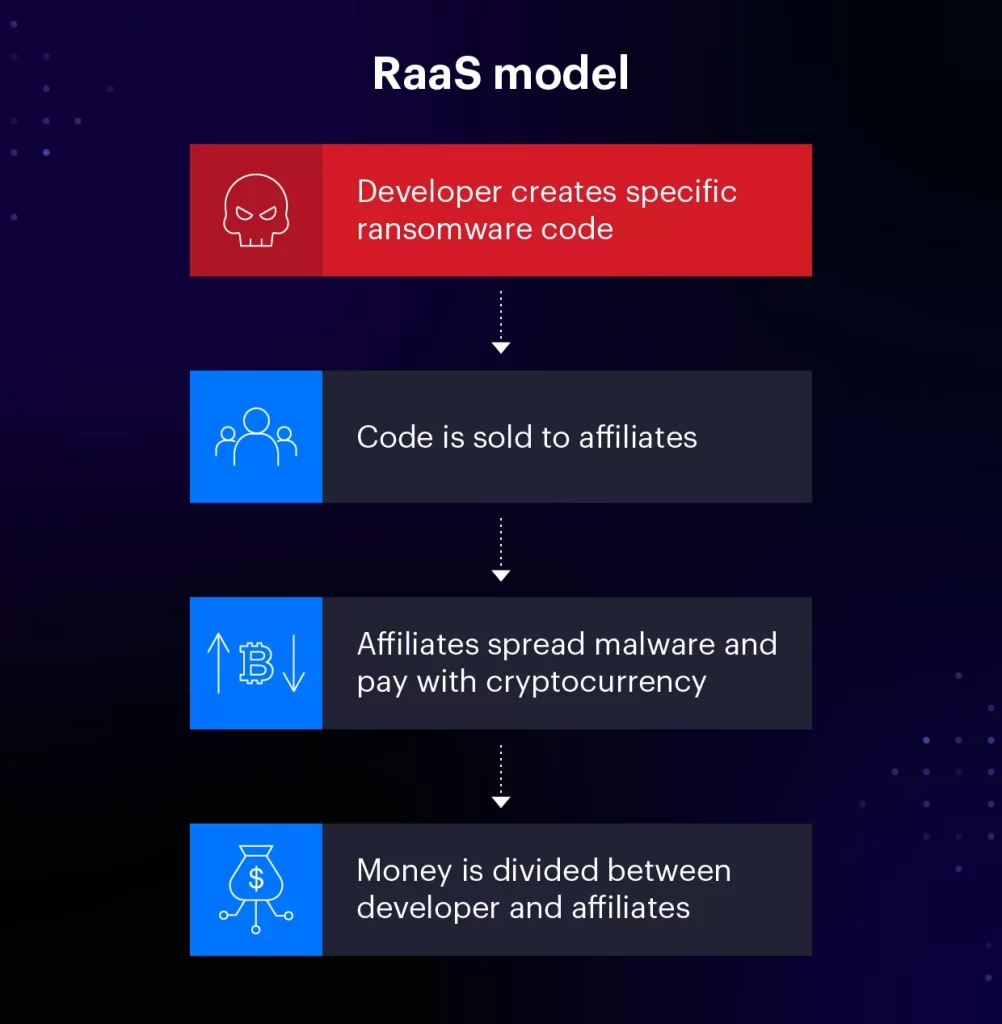
1. Ransomware-as-a-Service (RaaS) –
Ransomware as a service enables threat actors to encrypt the data of victims and demand ransom from them to provide them access to decryption keys so they can get access to their data back. Ransomware as a service providers typically offer services such as malware hosting, distribution, and support, making it easier for attackers to carry out ransomware attacks.
2. Banking Trojan-as-a-Service (BTaaS) –
Banking Trojan as a service is a type of malware as a service that is designed to steal financial information from victims. As the name suggests, this type of malware is used for spoofing financial information of banking customers including credit card numbers and passwords.
3. Remote Access Trojan-as-a-Service (RATaaS) –
Remote access trojan as a service allows an attacker to remotely control the infected computer and carry out malicious activities, such as data theft, surveillance, and unauthorized access to sensitive information.
4. Exploit-as-a-Service (EaaS) –
Exploit as a service provides cybercriminals with access to exploits that can be used to compromise computer systems and networks. This type of malware as a service is particularly dangerous because it allows attackers to take advantage of vulnerabilities in software and systems to carry out malicious activities.
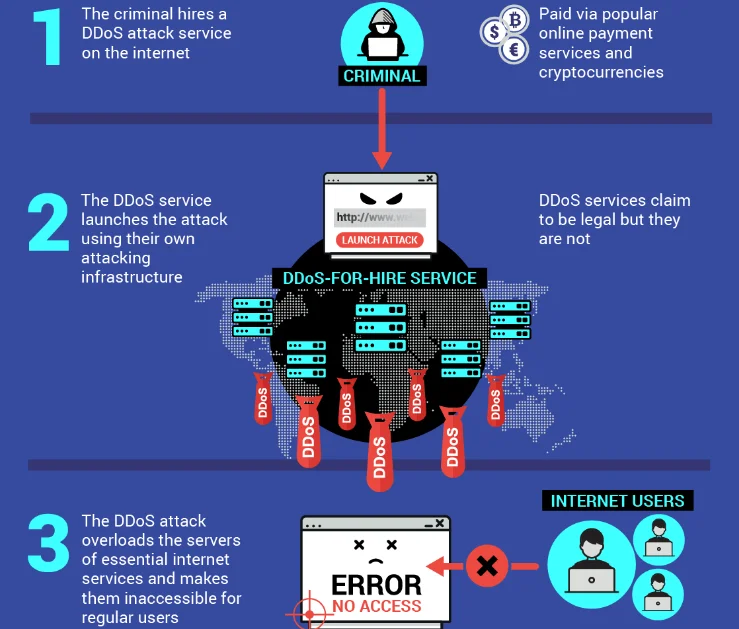
5. DDoS As a Service –
DDoS-as-a-Service allows an attacker to launch a DDoS attack against a target website or network. The primary objective behind DDoS attacks is to disrupt business operations. This could come in the form of making your website inaccessible by sending a flood of malicious traffic or can come in the form of disrupting a critical network or installation.
Malware as a service offerings come in many different forms and are becoming increasingly popular among cybercriminals. To protect against malware as a service attacks, it is important to adopt good security practices and invest in the appropriate security solutions. Stay vigilant and stay one step ahead of malware as a service provider.
Why Is Malware as a Service Becoming Popular With Cybercrimminals?
Malware as a service is becoming increasingly popular among cybercriminals because it allows them to carry out malicious activities without the technical expertise or resources needed to develop their own malware.
Malware as a Service Protection Strategies
1. Upgrade To Latest Version:
Make it a habit to update your software to the latest version as soon as the software provider launches the new version. Newer version comes with bug fixes, which minimize the security risk.
2. Use Anti-Malware Software:
Anti-malware tools are designed for a specific purpose, which is to block malware from infecting your system or bypassing your cybersecurity defenses. Run deep scans to identify any malware which is hiding under the radar.
3. Create Multiple Copies of Your Sensitive Data:
What if malware infects your systems and wreck havoc on your sensitive files? What course of action would you take? If you have a data backup, you can easily recover your data otherwise, you will find it tough to get your data back. That is why it is important for businesses to have a backup and disaster recovery plan
4. Role Based Access Control:
Implement role based access control so that every employee has only the required access needed to perform any task. Even if a threat actor succeeds in compromising an account, they will have limited access thanks to role based access controls.
5. Constant Monitoring:
Malware infections have their signs and symptoms. This means that it is easier to detect these inflections if you have continuous monitoring in place. Raise the red flag as soon as you experience suspicious and malicious behavior.
Conclusion
Malware as a service is a growing threat in the cybersecurity landscape and represents a significant risk to organizations and individuals. To protect against this type of attack, it is important to adopt good security practices and invest in the appropriate security solutions. How would you protect your business from malware as a service threat?






Add comment