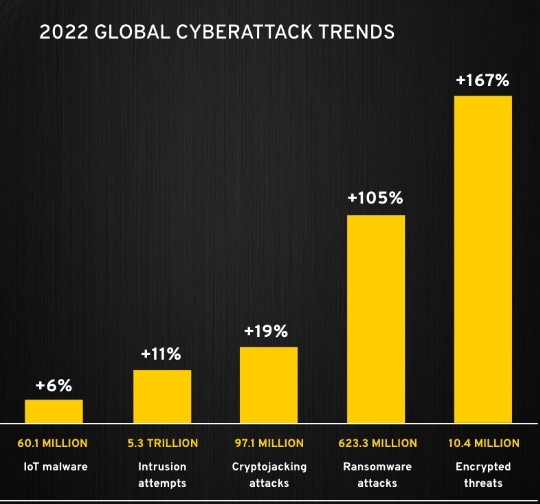
Did you know how frequently ransomware attacks target businesses? According to cybersecurity statistics, a ransomware attack takes place every 11 seconds. The average downtime experienced by businesses that come under a ransomware attack is 21 days. What’s even worse is that 80% of victims who submitted the ransom payments experienced another ransomware attack soon after.
In addition to this, 60% of businesses experienced revenue loss and 53% said that their brand reputation took a hit. The number of ransomware attacks targeting businesses is growing at an alarming rate. For the final nail in the coffin, cybercriminals have started offering ransomware as a service, which is why businesses need to know what it is and how can they stay protected from it.
In this article, you will learn what ransomware as a service is and how you can protect your business from it.
What is Ransomware as a Service?
According to Veronis, “Ransomware as a service is basically a subscription-based model that empowers affiliates to access specialized ransomware tools to execute ransomware attacks. Once you pay the subscription fee, you get access to affiliates who pay for the program.”
How You Can Protect Your Business From Ransomware Attacks?
Now that you know what ransomware as a service really is, let’s look at some of the ways you can protect your business from it.
1. Cybersecurity Training
The first step you need to take is to increase the cybersecurity awareness of your employees. The more aware your employees are, the less likely they are to fall victims to a ransomware attack. You can achieve this by organizing cybersecurity training programs that will not only educate but also train your employees on how to protect themselves from ransomware attacks by following the security best practices.
Just organizing cybersecurity training is not enough. Evaluate the effectiveness of the training program by asking participants to go through an exam to test their knowledge. Take feedback from your employees on how you can improve the training program. You can even launch mock ransomware attacks to see which employees fall victim to them and which ones don’t. This will give you a better idea about what they have learned from the training program.
2. Install Latest Software Patches
Cybercriminals are always on the lookout for loopholes and vulnerabilities to exploit. Once they find it, they waste little time taking advantage of them. One area where these vulnerabilities are present is outdated software. It contains bugs, errors and security loop holes that can easily be exploited by cybercriminals.

That is why it is important to plug all these software holes by installing software patches as soon as they are made available by software providers. These patches are released to plug in these vulnerabilities and fix errors and bugs that are present in the older versions of the software. If you are still using an older version of the software, update it to the latest version as soon as possible to mitigate the risk of vulnerability exploitation by hackers.
3. Take Regular Backup of Your Data
Did you know that the biggest ransomware mistake businesses make is failing to take backup of their data. Due to this, when they come under a ransomware attack, they have no choice but to pay the ransom to get their data back. Imagine having a backup of your data at your disposal and then coming under a ransomware attack. Can the attacker blackmail you into paying the ransom? No, right.
Even if you want to use passwords, it is highly recommended that you use multi-factor authentication. Yes, this might add an extra step and make user login less convenient for your users but it is more secure. This adds an extra layer of security on top so even if the hackers succeed in guessing or stealing your passwords, they won’t be able to access your data.
4. Constantly Monitor Logs
One of the easiest ways to detect ransomware attacks is to keep a close eye on your activity logs. If you are experiencing suspicious or malicious activity, this should serve as a red flag. Immediately report any such activity to the concerned department so they can take proactive action to minimize the damage. Delaying action can have far-reaching consequences. Maintain and monitor logs of all the activities in order to detect any malicious activity.

5. Be Proactive When It Comes To Threat Hunting
As hackers are aggressively looking for vulnerabilities to exploit, cybersecurity professionals should also be proactive with their threat hunting. Just because you have a threat hunting and intelligence program at your disposal does not mean that you can sit back and relax. These programs do work but they are still immature, which is why you should never solely rely on them for threat hunting. With proactive threat hunting, you can mitigate the risk before it becomes a bigger threat to your business.

7. Have an Incident Response Plan
Do you have an incident response plan to deal with cybersecurity attacks and data breaches? If you don’t, create one immediately. If you do have one, test its effectiveness. Identify gaps in your incident response plan and fill in those gaps to improve your incident response plan. You can conduct mock exercises that will help you assess the strengths and weaknesses of your incident response plans.
What steps do you take to protect your business from ransomware attacks? Let us know in the comments section below.





Add comment