The ever-expanding enterprise attack surface, easy execution, the growing popularity of ransomware as a service and financial reward has made ransomware a preferred attack vector for cybercriminals. Not only that, ransomware is also evolving. Previously, ransomware attacks usually targeted file-based systems but now it can also target databases and database servers.
What makes database ransomware more dangerous is the complicated recovery process and the requirement for database technology expertise. This means that businesses who don’t have staff who have an in-depth understanding of the database technologies powering these databases will find it tough to recover from database ransomware attacks.
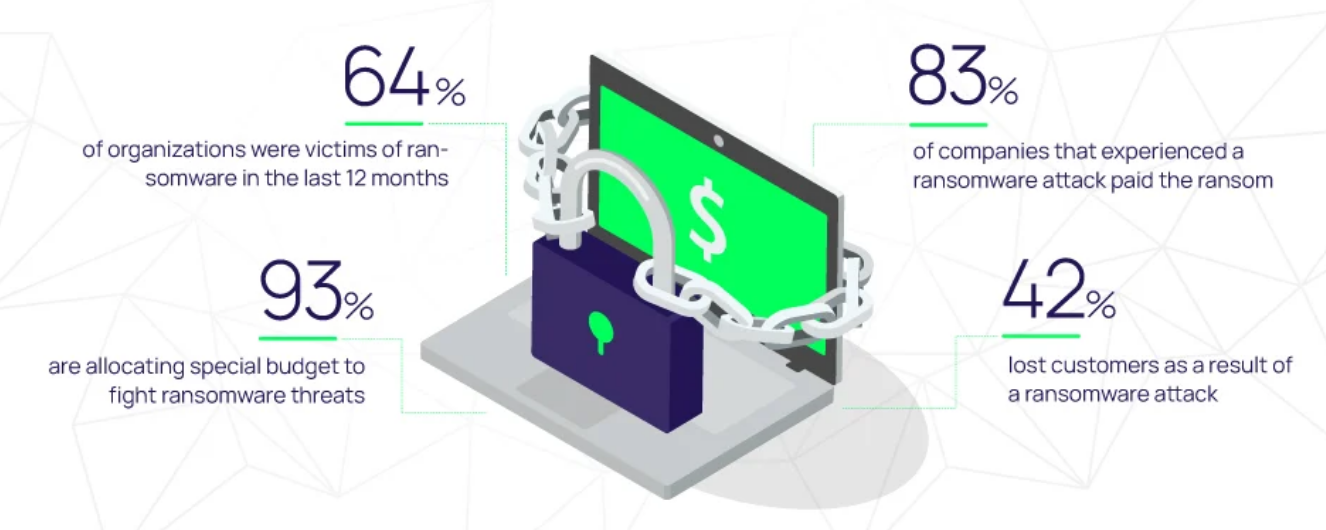
In this article, you will learn everything you need to know about database ransomware and what steps you can take to protect your business against it.
- Database Ransomware: Everything You Need To Know
- Encryption ransomware
- Exfiltration ransomware
- Hit and run attacker
- How To Detect Database Ransomware Attack?
- How To Recover From a Database Ransomware Attack?
- How To Restore Data After a Database Ransomware Attack?
- How To Mitigate Database Ransomware Attack?
Database Ransomware: Everything You Need To Know
What is a Database Ransomware Attack?
Database ransomware attacks target database objects instead of files. These types of ransomware attacks can be broadly classified into two different types:
- Encryption ransomware
- Exfiltration ransomware
Let’s look at each one in more detail to give you a better idea.
Encryption ransomware
In encryption ransomware attacks, a threat actor leverages built-in database functions and methods such as transparent data encryption or use traditional encryption standards such as AES, RSA, and DES to encrypt data before writing it to a disk.
Exfiltration ransomware
The primary purpose of exfiltration ransomware is to steal data. Threat actors can use database dumping tools, evasion techniques such as DNS exfiltration to fly under the radar and bypass security controls and use SELECT queries.
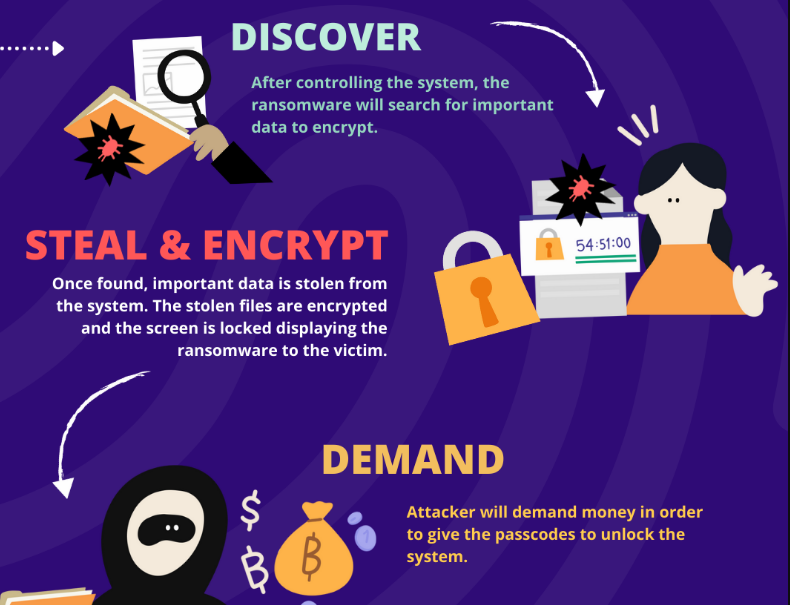
Types of Database Ransomware Attackers
- Hit and run attacker
- Resident attacker
Let’s look at each one to give you a better idea about how they operate.
Hit and run attacker
The “hit and run” attacker employs a rapid and disruptive approach to data encryption, displaying no concern for subtlety or persistence within the system. In this strategy, the threat actor uses generic database mechanisms that use primary encryption keys and secondary encryption keys. The primary key is used for encrypting the secondary key.
Subsequently, the attacker swiftly removes the primary encryption key, rendering the database unable to decrypt table data without the complete set of keys. The assailant executes this operation with speed and noise, likely utilizing database dumping tools or indiscriminate queries without filtering clauses to quickly access and encrypt the data before making a swift exit.
Resident attacker
The “resident” attacker employs a meticulous “slow & low” strategy, discreetly reading and comprehending data to avoid detection. Subsequently, the attacker encrypts the data but strategically leaves an encryption key intact to maintain the normal functioning of applications without immediate interference.
Once the data extraction is complete, the attacker removes the primary encryption key, rendering the information inaccessible. To further elude detection, the “resident” attacker incorporates evasion techniques, enabling a gradual and inconspicuous exfiltration of data while remaining under the radar.
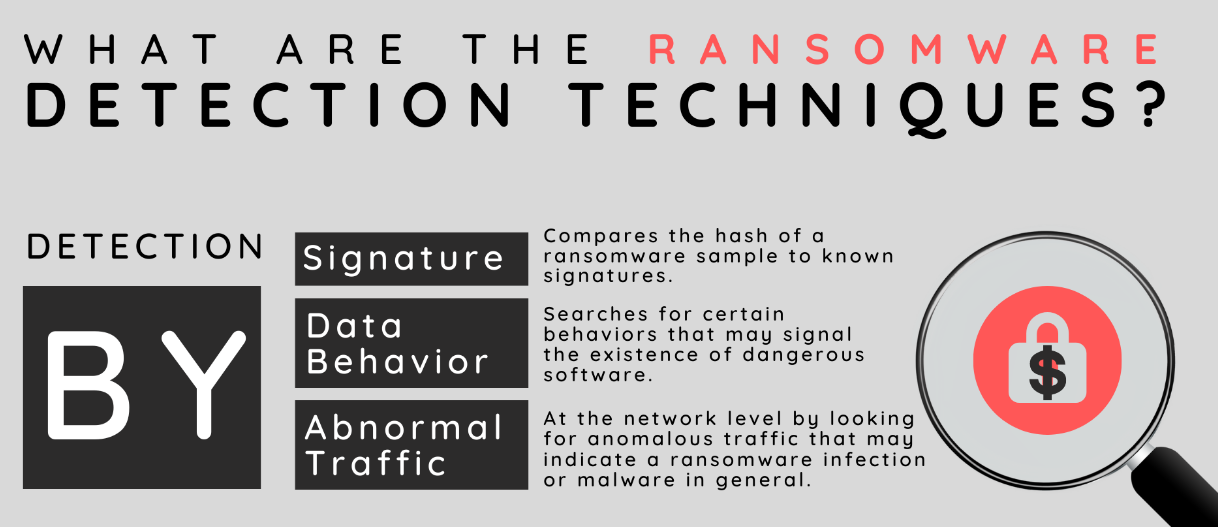
How To Detect Database Ransomware Attack?
Detecting a database ransomware attack early is crucial for minimizing damage. Organizations can employ a multi-layered database security approach, including:
a. Network Monitoring: Continuous monitoring of network traffic for unusual patterns or spikes in data encryption activities.
b. Anomaly Detection: Utilizing machine learning algorithms to identify abnormal behavior within the database system.
c. Endpoint Security: Implementing robust endpoint security solutions to detect and prevent ransomware installation on individual devices.
How To Recover From a Database Ransomware Attack?
Immediate response and recovery actions are essential when a database ransomware attack occurs. The following steps can be taken:
a. Leverage Network Segmentation: Create a separate network for day to day operations and sensitive business data. This will help you isolate the compromise devices and prevent the ransomware from affecting the other network.
b. Develop an Incident Response Playbook: Create an incident response plan and a playbook that highlight how to respond to particular threats.
c. Engage Law Enforcement: Report the attack to relevant law enforcement agencies for assistance and investigation.
d. Test Data Backup: Just having a backup is not enough. Test it continuously to ensure it is available when you need it the most.
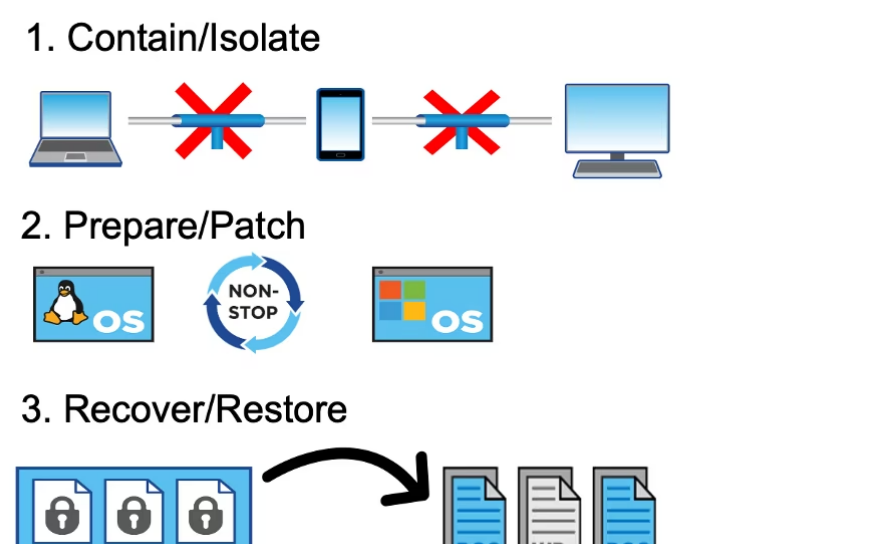
How To Restore Data After a Database Ransomware Attack?
Restoring data after a database ransomware attack involves the careful execution of a recovery plan:
a. Data Validation: Verify the integrity of backups to ensure they are free from malware.
b. System Rebuild: Rebuild compromised systems using clean backups and updated security measures.
c. Data Restoration: Gradually restore data to ensure the ransomware is completely eradicated.

How To Mitigate Database Ransomware Attack?
Adopt a proactive approach to cybersecurity and take security measures and it can go a long way in protecting your business from database ransomware attacks
- Install Patches Regularly: Install patches as soon as they are made available by software vendors.
- Access Control: Enforcing a strong access controls system is pivotal for minimizing the risk of privilege abuse and minimizing your enterprise.attack surface.
- Intrusion Detection Systems and Firewalls: Use web application firewall in conjunction with intrusion detection systems to block malicious traffic and threat actors from entering your network.





Add comment