According to the cost of data breach report, the average cost of a data breach is $4.35 million. That number is expected to jump to $5 million in 2023, according to Acronis prediction. With the cost of data breaches skyrocketing, it is important for businesses to know about the common attack vectors that lead to these data breaches so they can better protect themselves against these threats.
Are you interested in learning about the different attack vectors malicious threat actors use and what you can do to overcome them? In this article, you will learn everything you need to know about attack vectors from definition to types to how to overcome them.
- Attack Vectors: Everything You Need to Know
- What is an Attack Vector?
- How Do Attackers Exploit Attack Vectors?
- 1. Passive Attack
- 2. Active Attack
- What are Common Types of Attack Vectors?
- 1. Phishing
- 2. Ransomware
- 3. Distributed Denial of Service (DDoS) Attack
- 4. Compromised Credentials
- 5. Malware
- 6. Insider Threats
- 7. SQL Injection
- 8. Cross Site Scripting
- 9. Misconfiguration
- 10. Man in the Middle Attack
- 11. Lack of Encryption
- 12. Brute Force Attack
- 13. Unpatched Vulnerabilities
- 14. Trojan Horse
- 15. Session Hijacking
- 16. Zero Day Exploits
- 17. Third Party Vendors
Attack Vectors: Everything You Need to Know
What is an Attack Vector?
An attack vector is a means by which cyber attackers can gain unauthorized access to your network or computer systems so they can exploit vulnerabilities. Threat actors can use multiple attack vectors simultaneously to steal user credentials, cause a data breach or exploit loopholes in your cybersecurity systems.
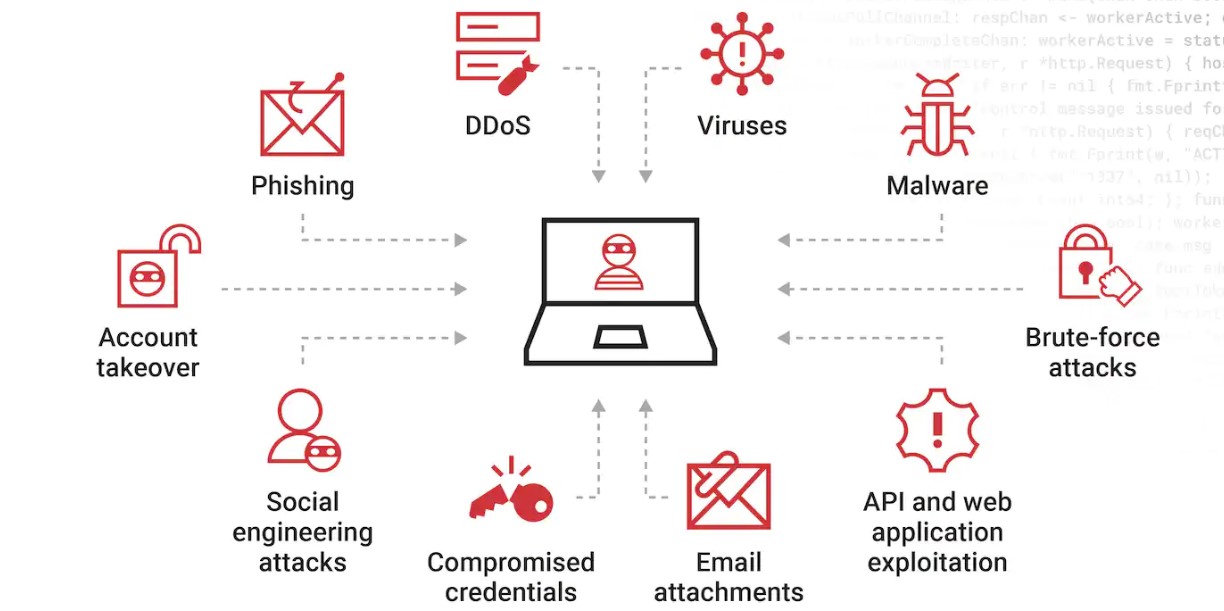
How Do Attackers Exploit Attack Vectors?
Cybercriminals use two methods to exploit attack vectors. They can launch a
- Passive Attack
- Active Attack
Let’s look at each one in more detail to give you a better idea about them.
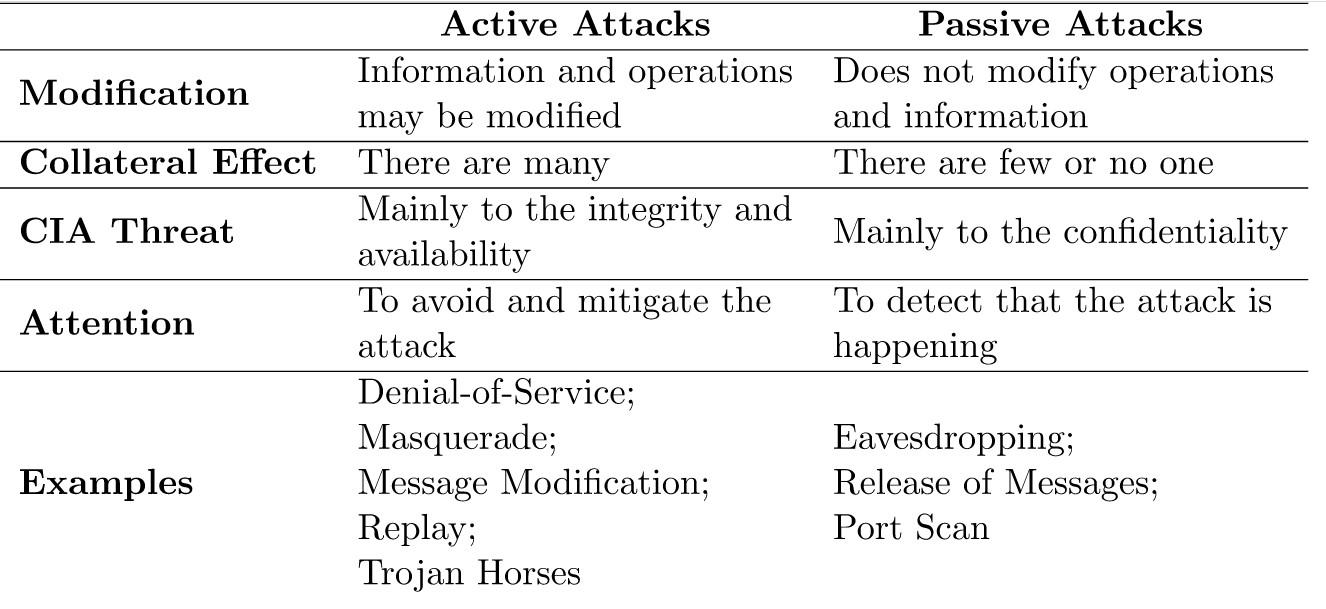
1. Passive Attack
A passive attack is a type of attack in which the cyberattacker tries to gain access to your system without affecting the system resources and data. That is why it is more difficult to detect a passive attack. The attacker silently monitors your systems for vulnerabilities and open ports they can exploit. This could involve session capture and port scans as well as active reconnaissance. Some of the best examples of passive attacks are phishing attacks and social engineering attacks.
2. Active Attack
An active attack is launched by cybercriminals to disrupt operations, damage the organization system or cause harm to system resources. Some of the best examples of active attacks are denial of service attack, ransomware, malware, domain hijacking or man in the middle attack.
What are Common Types of Attack Vectors?
There are many different types of attack vectors. Some of them are as follows:
1. Phishing
Phishing is a form of social engineering attack that involves deceiving users into divulging sensitive information, such as passwords or credit card details, by disguising themselves as a trustworthy source via email, phone, or social media. Attackers use phishing emails with malicious links or attachments to lure victims into sharing their credentials or downloading malware onto their system. These types of attacks can be devastating for both individuals and organizations, as attackers can use the stolen information to gain unauthorized access to sensitive data and systems.
2. Ransomware
Ransomware is a type of malicious software that encrypts a victim’s files or system and demands payment in exchange for the decryption key. The attack often begins with a phishing email or through exploiting unpatched vulnerabilities in a system, allowing the attacker to gain access to the victim’s files or network. Once the attacker has gained control of the system, they will typically leave a ransom note with instructions on how to pay the ransom in order to receive the decryption key. Ransomware attacks can be very costly, both financially and in terms of lost productivity and data.
3. Distributed Denial of Service (DDoS) Attack
A Distributed Denial of Service (DDoS) Attack is a type of cyber attack that involves overwhelming a target system or network with a flood of traffic from multiple sources. This attack typically involves the use of a botnet, which is a network of infected computers that are controlled by the attacker to carry out the attack. The goal of a DDoS attack is to make a system or network unavailable to its intended users, causing disruption or damage to the targeted organization’s operations.

4. Compromised Credentials
Compromised credentials occur when an attacker gains unauthorized access to a user’s username and password, either through phishing or some other means. With this information, the attacker can gain access to sensitive information, such as bank accounts, email accounts, or other personal data. Compromised credentials are a common way for attackers to gain access to systems and networks, as many users use the same username and password across multiple accounts, making it easy for attackers to gain access to multiple systems.
5. Malware
Malware is a broad term that encompasses any type of software that is designed to harm or exploit a system or network. Malware can be delivered through a variety of means, including email attachments, malicious websites, or infected software downloads. Once installed, malware can carry out a variety of harmful actions, such as stealing sensitive data, destroying files, or giving the attacker control over the victim’s system.
6. Insider Threats
Insider Threats refer to malicious activities carried out by individuals who have authorized access to an organization’s systems and data. These individuals may be current or former employees, contractors, or partners who have been granted access to the organization’s systems. Insider threats can be particularly damaging, as insiders often have knowledge of the organization’s systems and may be able to bypass security measures more easily than an outside attacker.
7. SQL Injection
SQL Injection is a type of attack that involves exploiting vulnerabilities in a website or application that uses a database to store information. This attack involves injecting malicious SQL code into an input field on a website, which can allow an attacker to gain access to the database or execute other malicious actions.

8. Cross Site Scripting
Cross Site Scripting (XSS) is another type of attack that targets websites and applications. This attack involves injecting malicious code into a web page, which is then executed by the victim’s browser. The attacker can use this code to steal information, such as login credentials or sensitive data, or to carry out other malicious actions.
9. Misconfiguration
Misconfiguration is a common vulnerability that can be exploited by attackers. This involves the improper configuration of systems, software, or networks, which can allow attackers to gain unauthorized access or execute malicious actions.
10. Man in the Middle Attack
Man in the Middle (MitM) Attacks involve intercepting communications between two parties, such as a user and a website. The attacker can then monitor or modify the communication, potentially stealing sensitive information or data.

11. Lack of Encryption
Lack of encryption refers to the absence of encryption protocols that protect sensitive data in transit or at rest. Attackers can intercept, steal, and tamper with this data if it is not properly encrypted. This can happen through a variety of means, such as eavesdropping on network traffic, stealing unencrypted data from storage devices, or compromising unencrypted communication channels.
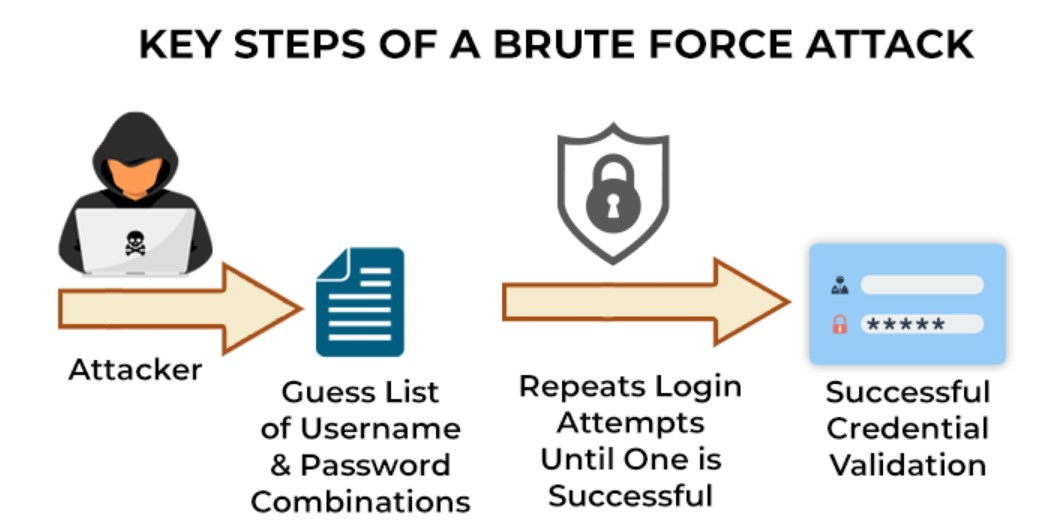
12. Brute Force Attack
A Brute Force Attack is a type of attack that involves an attacker attempting to guess a password or encryption key by trying a large number of possible combinations until the correct one is found. Brute force attacks can be very time-consuming and resource-intensive, but they can be successful if the password or key is weak or poorly chosen.
13. Unpatched Vulnerabilities
Unpatched vulnerabilities are security flaws in software, systems, or networks that have been identified but not yet fixed. Attackers can exploit these vulnerabilities to gain unauthorized access or carry out malicious actions. The longer a vulnerability remains unpatched, the greater the risk of a successful attack.
14. Trojan Horse
A Trojan Horse is a type of malware that disguises itself as legitimate software to trick users into installing it. Once installed, the Trojan can carry out a variety of malicious actions, such as stealing sensitive information, giving the attacker control over the victim’s system, or installing additional malware.
15. Session Hijacking
Session Hijacking involves an attacker taking control of a user’s active session on a website or application. This can be done through a variety of means, such as stealing the user’s session cookie or using a network sniffer to intercept the session data. Once the attacker has control of the session, they can carry out actions on behalf of the user, potentially accessing sensitive information or carrying out malicious actions.
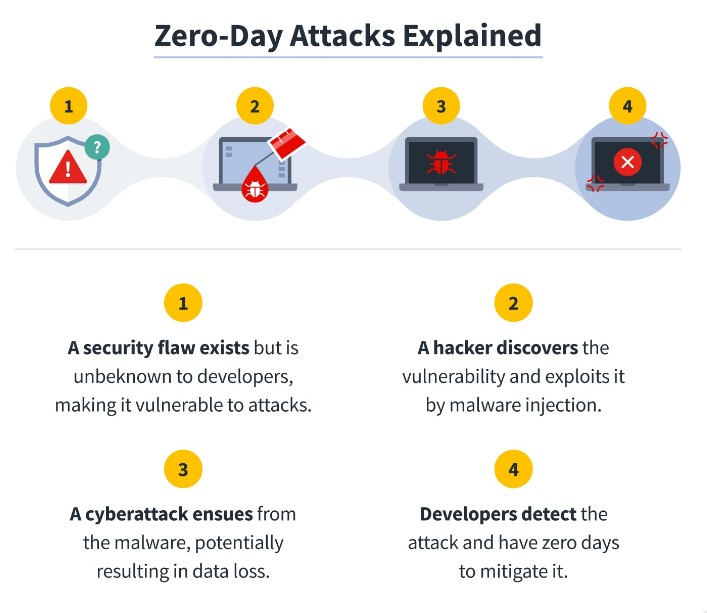
16. Zero Day Exploits
Zero-day exploits are attacks that target vulnerabilities that are unknown to the software vendor or security community. These vulnerabilities are called “zero day” because they are discovered and exploited by attackers before a patch or fix can be developed. Zero day exploits can be very dangerous, as they can be used to carry out targeted attacks against specific individuals or organizations, and they also remain undetected for long periods of time.
17. Third Party Vendors
Third Party Vendors are companies that provide goods or services to an organization but are not directly controlled by the organization. Third party vendors can be a significant security risk, as attackers can target these vendors to gain unauthorized access to the organization’s systems or data. It’s important for organizations to carefully vet their third party vendors and ensure that they have strong security measures in place.
Which of these attack vectors have impacted your business the most? What steps did you take to overcome it? Share it with us in the comments section below.





Add comment