Malware, short for malicious software, is any program or file that is designed to harm or exploit a computer system. There are many different types of malware, each with its own unique characteristics and behavior. In this article, you will learn about ten common types of malware and how to protect your business from them.
10 Common Types of Malware Your Business Should Guard Against
Here are 10 common types of malware that you should guard against:
1. Viruses:
A computer virus is a type of malware that attaches
itself to a program or file, and can replicate itself to other computers. Once a virus infects a computer, it can cause a wide range of problems, including slowing down or crashing the system, deleting or corrupting files, and stealing personal information. Viruses can also spread through email attachments, instant messaging, and infected software downloads.
2. Trojan horses:
A Trojan horse is a type of malware that disguises itself as legitimate software. It is often used to trick users into downloading and installing it on their computer. Once a Trojan horse is installed, it can give hackers access to the infected computer, allowing them to steal personal information, install other malware, or take control of the computer. Trojans can also spread through email attachments, instant messaging, and infected software downloads.
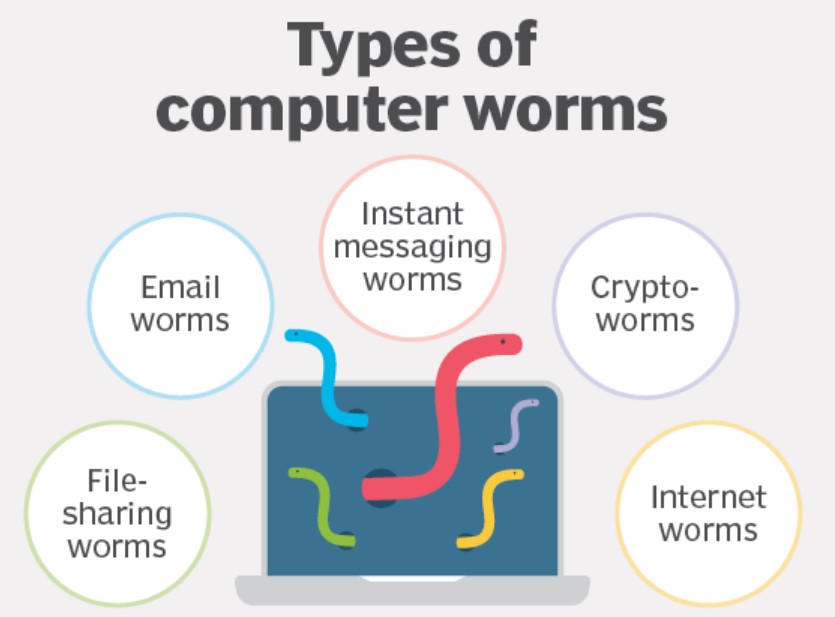
3. Worms:
A worm is a type of malware that is designed to spread itself to other computers. It can replicate itself without any user interaction, and can exploit vulnerabilities in operating systems or software to spread. Worms can cause widespread damage by consuming network bandwidth and clogging up computer systems. They can also spread through email attachments, instant messaging, and infected software downloads.
4. Ransomware:
Ransomware is a type of malware that encrypts a victim’s files, making them inaccessible. It then demands payment, usually in the form of a cryptocurrency, in exchange for the decryption key. Ransomware attacks can be particularly devastating for individuals and businesses, as they can lose access to important data and files. Ransomware can be delivered via various vectors such as email attachments, infected websites, social engineering, or software vulnerabilities.
5. Adware:
Adware is a type of malware that displays unwanted advertisements on a computer. It is often bundled with free software, and can be difficult to remove. Adware can be particularly frustrating, as it can cause pop-up ads and unwanted browser redirects. It can also be used to track a user’s browsing habits, which can lead to targeted advertising and privacy concerns.
6. Spyware:
Spyware is a type of malware that is designed to collect personal information without the user’s knowledge or consent. It can track a user’s browsing habits, log keystrokes, and even record audio and video. Spyware can also be used to steal personal information, such as login credentials or credit card numbers.

7. Rootkits:
A rootkit is a type of malware that is designed to hide itself and other malware on a computer. Rootkits can be difficult to detect and remove, making them a serious threat to security. They can be used to gain unauthorized access to a computer and steal personal information, or to install other malware. Rootkits can also be used to evade detection by security software.

8. Fileless malware:
Fileless malware is a type of malware that resides only in memory, and does not leave any traces on the hard disk. This type of malware is difficult to detect and remove, and can be used for various malicious purposes, such as stealing personal information, or to establish a foothold in a target’s network to perform further attacks.
Bots are automated software programs that can be used for malicious purposes, such as Distributed Denial of Service (DDoS) attacks. In addition to this, DDoS attacks can be used to take down websites or network infrastructure by flooding them with traffic from a large number of bots. Bots can also be used to perform automated tasks, such as scraping data from websites, or spreading spam or malware.
10. Mobile malware:
Mobile malware is a type of malware that targets mobile devices, including smartphones and tablets. It can take many forms, such as viruses, Trojan horses, and spyware, and can be delivered via various vectors, such as infected apps, email attachments, and malicious websites. Some common types of mobile malware include:
- SMS Trojans: These are malicious apps that can send text messages to premium numbers without the user’s knowledge or consent. They can also steal personal information, such as contact lists and login credentials.
- Adware: Adware can display unwanted ads and cause unwanted browser redirects on mobile devices, as well as tracking a user’s browsing habits and collecting personal information.
- Banking Trojans: These are malicious apps that can steal login credentials, credit card numbers, and other personal information from mobile banking apps.
- Spyware: Spyware can track a user’s location, record audio and video, and steal personal information.
It is important to note that mobile malware can have severe consequences, such as financial loss, identity theft and privacy breaches. To protect yourself from mobile malware, it is important to only download apps from trusted sources, such as the Apple App Store or Google Play Store, and to be cautious of any suspicious emails or text messages that ask you to download an app or click on a link. Additionally, you should keep your mobile device software updated, and use a mobile security app to scan for malware and protect your device.
It is important to note that malware can be delivered via various vectors such as email attachments, infected websites, social engineering attacks or software vulnerabilities. To protect yourself from malware, it is important to use anti-virus software and keep it updated, be wary of suspicious emails and links, and keep your operating system and software updated. Additionally, you should be mindful of your online behavior and be aware of the common tactics used by cybercriminals to spread malware.
Which of these malware have targeted your business and how did you get rid of it? Share it with us in the comments section below.





Add comment