In the digital world, DDoS attacks are a prevalent and disruptive form of cyberattack, jeopardizing network and online service accessibility. Understanding the types of DDoS attacks is vital for protection and preparation against these malicious activities. This article explores three common types of DDoS attacks and their impact on targeted systems.
- 3 Common Types of DDoS Attacks
- 1. Volume-Based Attacks:
- ● UDP Floods:
- ● ICMP Floods:
- ● Spoofed Packet Floods:
- ● DNS Amplification Attacks:
- 2. Protocol Attacks:
- ● SYN Flood:
- ● Ping of Death:
- ● Smurf DDoS Attack:
- 3. Application Layer Attacks:
- ● Slowloris Attacks:
- ● GET/POST Floods:
- How To Protect Against Different Types of DDoS Attacks?
- Conclusion
3 Common Types of DDoS Attacks
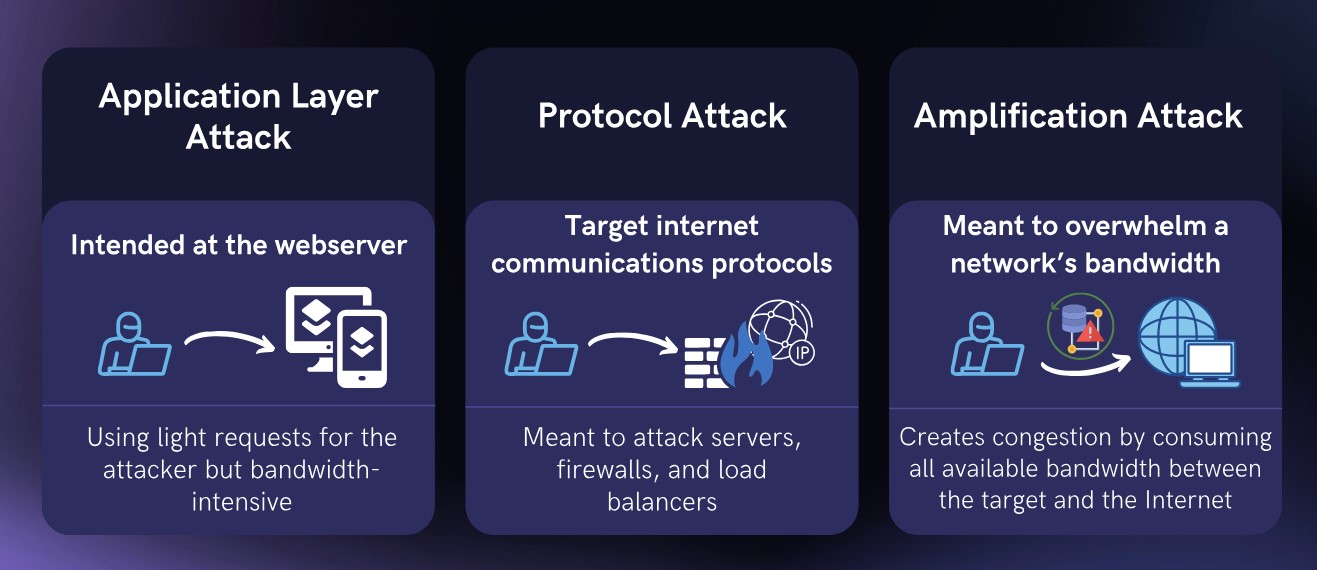
There are three main types of DDoS attacks
- Volume Based Attacks
- Application Layer Attacks
- Protocol Attacks
1. Volume-Based Attacks:
Volume-based DDoS attacks aim to saturate the target network’s bandwidth, consuming all available resources and rendering the system unable to respond to legitimate traffic.
Here are four commonly encountered volume-based attacks:
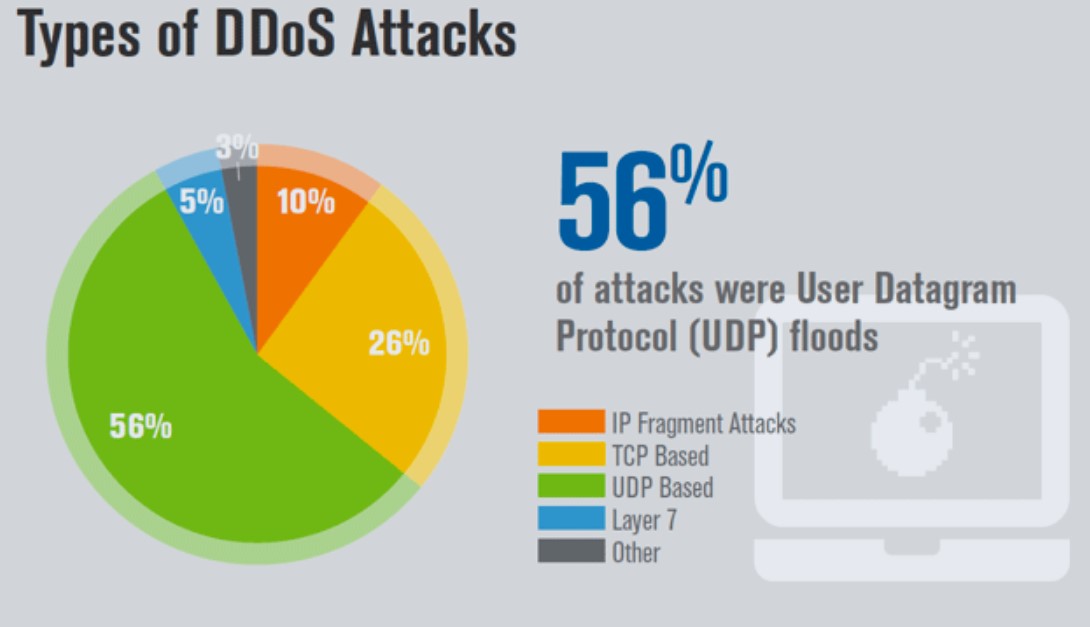
● UDP Floods:
User Datagram Protocol (UDP) floods the target system with a large number of UDP packets, overwhelming its ability to handle incoming requests. Since UDP is connectionless, attackers can easily send spoofed or falsified requests, making it challenging for the target to filter out malicious traffic.
● ICMP Floods:
Internet Control Message Protocol (ICMP) floods exploit vulnerabilities in the ICMP protocol, which is responsible for network diagnostics and error reporting. Attackers flood the target with ICMP Echo Request (ping) packets, overwhelming the system’s processing capabilities and causing network congestion.
● Spoofed Packet Floods:
In spoofed packet floods, attackers forge the source IP addresses of the packets, making it difficult for the target to identify the true source of the attack. By flooding the target system with a high volume of packets, the attackers exhaust its resources and disrupt its normal functioning.
● DNS Amplification Attacks:
These attacks exploit vulnerable DNS servers by sending a small number of requests that result in a large volume of response traffic. Securing DNS servers by disabling recursive queries for external clients and implementing rate limiting can help protect against DNS amplification attacks.
2. Protocol Attacks:
Protocol-based DDoS attacks exploit vulnerabilities in the network protocols used by the target system. These attacks consume server resources by exploiting the way protocols establish and maintain connections.
Here are three common protocol-based attacks:
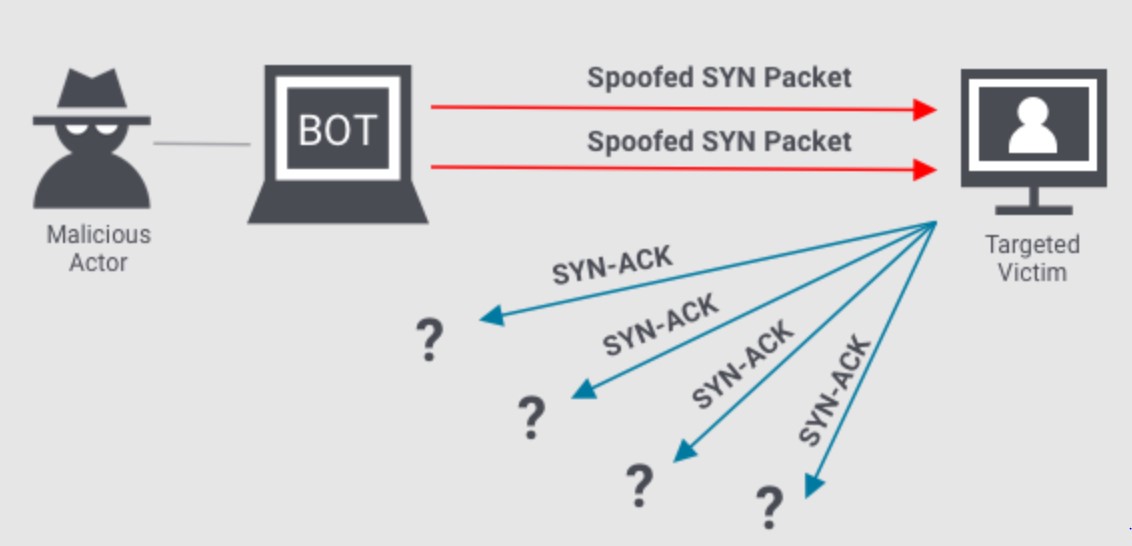
● SYN Flood:
SYN Flood attacks exploit the three-way handshake process used by the Transmission Control Protocol (TCP) to establish a connection. Attackers send a flood of SYN requests to the target, but never complete the handshake process by sending the expected ACK packets. This exhausts the target’s resources as it waits for responses that will never arrive, rendering it unable to establish legitimate connections.
● Ping of Death:
Ping of Death attacks abuse the ICMP protocol by sending oversized ICMP Echo Request (ping) packets to the target system. These packets are larger than the standard size allowed by the protocol, causing buffer overflows and system crashes. This attack can disrupt the target’s network connectivity and potentially crash the system.
● Smurf DDoS Attack:
Smurf attacks exploit the Internet Control Message Protocol (ICMP) and the Internet Protocol (IP) broadcast addresses. Attackers send ICMP Echo Request (ping) packets to IP broadcast addresses, which then reflect and amplify the attack by flooding the target with numerous ICMP Echo Replies. This can overwhelm the target’s network resources and cause a denial of service.
3. Application Layer Attacks:
Application layer DDoS attacks target the application layer of a network stack, focusing on exhausting resources within the target application itself. These attacks are particularly challenging to mitigate since they mimic legitimate user behavior.
Here are two common application layer attacks:
● Slowloris Attacks:
Slowloris attacks exploit the way web servers handle concurrent connections by keeping multiple connections open but sending HTTP headers at a very slow pace. To protect against Slowloris attacks, web servers can be configured to limit the number of concurrent connections from a single IP address and enforce timeouts for idle connections.
● GET/POST Floods:
GET/POST Flood attacks overwhelm the target system’s resources by sending a high volume of GET or POST requests to a specific application. These requests consume server resources such as CPU, memory, and disk I/O, leading to a significant performance degradation or service disruption.

Being aware of these common types of DDoS attacks is crucial for businesses to establish robust defensive measures
How To Protect Against Different Types of DDoS Attacks?
Adopting a multi-layered defense strategy can enhance protection against DDoS attacks. This includes having redundant network infrastructure, implementing traffic monitoring and anomaly detection systems, employing content delivery networks (CDNs) for distributing traffic, and using cloud-based DDoS mitigation services. Regular security audits, network testing, and employee training on security best practices are also essential to maintain a robust defense against DDoS attacks.
Conclusion
DDoS attacks remain a significant threat, with volumetric, application-layer, and protocol attacks being prevalent. Robust cybersecurity measures like traffic monitoring and firewalls are crucial for detection and mitigation. Collaboration among stakeholders is essential in combating DDoS attacks and ensuring a safer digital environment. Vigilance and proactive defense strategies can mitigate DDoS attack impacts and enhance online resilience.
Did this article help you in understanding common types and sub types of DDoS attacks? Share it with us in the comments section below.





Add comment