A distributed denial of service attack is a cyber attack where a large volume of malicious traffic is sent to a target server to stop the server from functioning normally. The aim of a DDoS attack is to disrupt normal operations of a service or network and the main purpose behind DDoS attacks is to cause monetary loss, damage and gain publicity.
Today, DDoS attacks rank among the most common and disruptive of cyber attacks. A DDoS attack can target any kind of network, from public corporations to private businesses and systems that manage essential infrastructure. DDoS attacks are becoming more common. According to DDoS attack statistics, more than 23,000 DDoS attacks were recorded every day. This translates into 16 DDoS attacks every minute.
Some might even call them the new norm. DDoS attacks are scary and something that you definitely want to avoid. However, for many organizations and businesses, it is not easy to avoid them and will come across them sooner or later. In this article, you will learn about four stages of DDoS mitigation and how your business can use it to safeguard your business against DDoS attack.
What is DDoS Mitigation?
DDoS mitigation is the process of safeguarding a target from distributed denial of service attack successfully. The primary objective of DDoS mitigation is to filter out malicious traffic and prevent DDoS attacks from reaching the target.
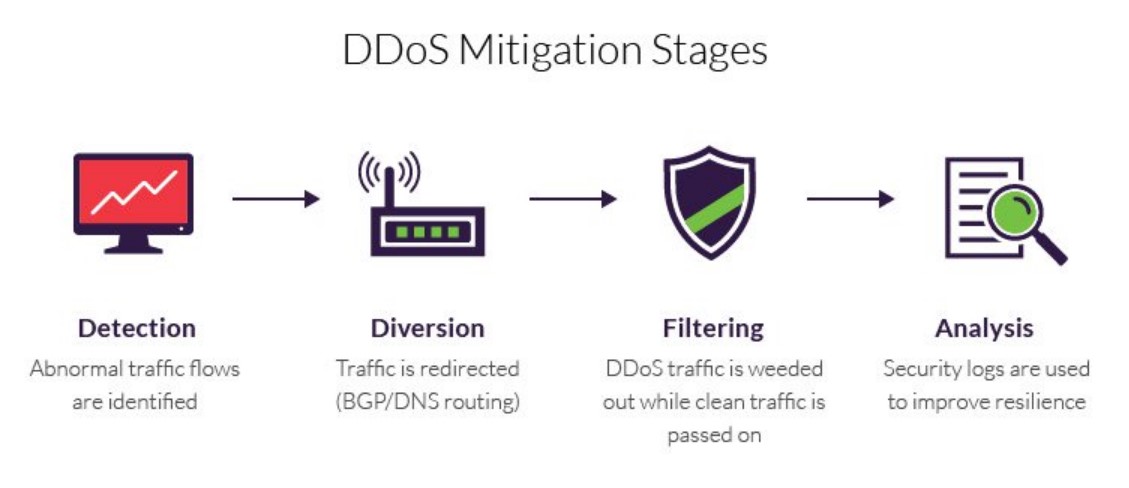
4 Stages Involved In DDoS Mitigation
There are four stages involved in the DDoS mitigation process.
1. Detect
The first phase of a DDoS mitigation process is detection. During this phase, the DDoS mitigation service providers look at warning signs and red flags that could indicate a DDoS attack. The effectiveness of the detection usually rests on how early you can detect the threat. The earlier you can detect a distributed denial of service attack, the better. This gives you more time to respond to DDoS attacks and minimize the damage to a certain degree.
2. Divert
Once you have detected a DDoS attack, the next step is to divert the flood of malicious traffic. You need to reroute malicious traffic away from the target server by harnessing the power of DNS (Domain Name System) or BGP (Border Gateway Protocol) rerouting. At this stage, you need to decide whether you should filter the traffic or discard it altogether.

One of the biggest advantages of DNS routing is that it is effective against both application layer and network layer attacks. In addition to this, it is always enabled and can respond to attacks in a more effective and timely manner. On the flipside, BGP rerouting can either be in an always on or on-demand state. What’s even worse is that BGP rerouting can also lead to more complexity, especially when it comes to routing updates.
3. Filter
If you have decided to filter out the malicious traffic instead of discarding it, the next step would be to apply filters to differentiate malicious traffic from legitimate traffic. DDoS mitigation solutions accomplish this by identifying patterns in different types of legitimate traffic such as human based traffic, malicious traffic, API calls, traffic from search engine bots, etc.
One of the biggest challenges for DDoS mitigation services is how they can mitigate DDoS attacks without negatively impacting the user experience. The best DDoS protection usually works in the background without letting site visitors notice any performance slowdowns. As a business, you don’t want your users to feel the pinch of a DDoS attack because it not only leaves a bad taste in their mouth as far as user experience goes but it will also dent your brand reputation.
4. Analyze
After you have successfully applied filters and separated legitimate traffic from malicious ones, the last step is to collect information and analyze it. You need to monitor system logs so you can gather data about the attack and attackers. This also gives you a clue about what to expect from future attacks and puts your business in a better position to combat future attacks.
Even though maintaining system logs is an old method, it is still being used by many businesses who are still stuck with legacy systems. The problem with that approach is that it does not give you real time insights. In today’s fast paced cybersecurity arena, you need real time insights to respond to attacks in an efficient manner.
It is highly recommended that you invest in modern security analytics and DDoS mitigation tools and adopt the latest DDoS mitigation techniques to gain complete visibility into malicious traffic. This will make it easy for you to develop a better understanding of different threat and attack vectors. The more control, insights and visibility you have, the better would be your response against a DDoS attack.
How do you mitigate DDoS attacks in your organization? Share it with us in the comments section below.





Add comment