Black Hat Conferences have built a reputation for gathering security professionals from around the globe. They are especially famous for presenting innovative research and investigative analysis of security flaws, vulnerabilities, cybersecurity attacks and data breaches for the past 25 years. This year was no different.
Black Hat 2022 pulled the curtain over the latest enterprise security trends that will impact enterprises in 2023 and beyond. Chris Krebs, founding fathers and former director of Cybersecurity and Infrastructure Security Agency (CISA) summed it brilliantly in his keynote address at Black Hat 2022 Conference when he said, “The more complex your tech stack is and the more it relies on implicit trust, the easier it is for hackers to hack it.”
According to Krebs, governments and enterprises are not doing enough to curb supply chain attacks, which is evident from attacks such as SolarWinds. He further added that companies that are shipping software products are actually shipping targets for hackers and cybercriminals to hit.
If you are interested in learning more about the latest enterprise security trends that will dominate in 2023 then, this article is for you. In this article, you will learn about five emerging enterprise security trends you cannot afford to ignore in 2023, according to Black Hat 2022.
5 Futuristic Enterprise Security Trends You Should Pay Attention To In 2023
Here are five enterprise security trends that will impact every enterprise in 2023.
1. Reduce Enterprise Attack Surface
As enterprises grow, so do their enterprise attack surfaces. New devices, new roles and new nodes are added every day, which not only increase complexity but also vulnerability. The bigger your enterprise attack surface, the more opportunities cybercriminals have to target your business. That is why it is important to take steps to minimize your enterprise attack surface.
Before making any move, it is better to outline your enterprise attack surface. Once you have a clear idea about how large your enterprise attack surface actually is, you should enforce strict access management policies and systems such as identity and access management, privilege access management and secure continuous integration and continuous delivery pipeline.
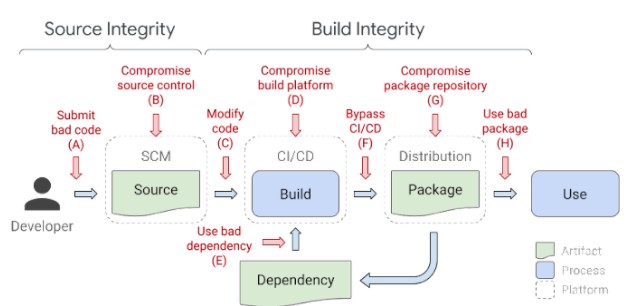
Cybercriminals can exploit vulnerabilities in source code management systems for privilege escalation and get the ability to move laterally through your network. This allows them to wreak havoc on code repositories and get their hands on the supply chain both at the same time.
Implement stringent patching and update policies and segment your network into two parts. Ensure compliance, hire auditors and beef up the security of your emails. Take regular backup of your critical data. All these will go a long way towards helping you reduce the size of your enterprise attack surface.
2. API Security Takes Center Stage
One area where most enterprises lag far behind is API security. Vendors and API security solution providers have also identified it as an opportunity. This is why we see many vendors such as Checkmarx, Contrast Security, Canonic Security, Cybersixgill, Traceable, and Veracode unveil their API security solution at Black Hat 2022 Conference.

These API security solutions not only detect malicious and unknown application programming interfaces but are also capable of performing remediation operations. Some can even prevent malicious API bots and safeguard against misuse and fraud. Not only that, some are even capable of anticipating API-based attacks.
3. Supply Chain Attacks Will Continue To Rise
With over 300 vendors showcasing their new products at the Black Hat 2022 conference, you might be expecting a diversified set of products but that was not the case. Majority of products focused on DevOps, zero trust and continuous integration and continuous delivery. One common theme among all these solutions is that most of them are designed to block supply chain attacks.

You can gauge the severity of the supply chain attack problem by the fact that NIST is changing its guidelines and standards to better cope with supply chain attacks. Cycode, known for their supply chain security, introduced container scanning capabilities along with application security testing capabilities to its existing platform.
Veracode, famous for their security testing solutions, also added a host of new changes to its continuous software security platform. Some of them include changes to API, Software Bill of Materials, added support for software composition analysis and added support for new frameworks such as Ruby 3.x, Rails 7.0 and PHP Symfony.
4. Artificial Intelligence Will Make A Huge Difference
By far the biggest announcement at the Black Hat 2022 Conference was CrowdStrike’s industry-first AI-powered Indicators of Attack (IOAs). Indicators of attack solutions can help you prevent data breaches by enabling you to analyze the behavior of the threat actor.
The tool harnesses the power of cloud native machine learning and fuses it with human expertise to help you identify the malicious intent of threat actors and what techniques they use to fulfill their malicious goals. When you combine the cloud native machine learning models powered by telemetry data with the expertise of threat hunting teams, you get a formidable tool that can help you analyze huge data sets with accuracy and speed thanks to AI and machine learning capabilities.

What really makes CrowdStrike offering special is that it can even identify newer adversary patterns which have never been tracked before. Amol Kulkerni, chief product and engineering officer at CrowdStrike proudly claimed, “CrowdStrike leads the way in stopping the most sophisticated attacks with our industry-leading indicators of attack capability, which revolutionized how security teams prevent threats based on adversary behavior, not easily changed indicators.”
5. Open Cybersecurity Schema Framework
One of the common problems most cybersecurity leaders encounter when it comes to extended detection and response, cybersecurity monitoring and endpoint management is lack of a common standard to enable alerts across different platforms. Thankfully, this issue has now been resolved thanks to Open Cybersecurity Schema Framework.
More than a dozen leading vendors including IBM, AWS, Splunk, CrowdStrike and Palo Alto Networks decided to collaborate to develop a common framework and they ended up creating the Open Cybersecurity Schema Framework project. This helped organizations in streamlining security data spread across a wide variety of security products and services.
Which enterprise security trend will create the biggest impact in your opinion? Share it with us in the comments section below.





Add comment