2022 was the year where we saw a record number of cybersecurity attacks and data breaches. Don’t expect 2023 to be much different. Cyberattackers will continue their relentless assault on business while cybersecurity professionals will look for ways to protect the critical business assets.
If you are wondering which cybersecurity threats could create the most problems for your business then this article is for you. In this article, you will learn about seven cybersecurity risks that you can not afford to ignore in 2023.
10 Dangerous Cybersecurity Risks You Can Not Afford To Ignore In 2023
Here are ten dangerous cybersecurity risks you can not ignore in 2023.
1. Supply Chain Attacks
According to the cost of data breach report 2022 by IBM, 19% of all data breaches resulted in supply chain attacks. What’s even more alarming is that the cost of data breach due to supply chain attacks is much higher than the average cost, which stood at $4.46 million.
Unfortunately, cybersecurity experts predict that supply chain attacks will only get worse in 2023. Expect to see the numbers, severity and frequency of supply chain attacks go up in 2023. Businesses will have to adopt a zero trust approach in order to minimize the impact of these supply chain attacks. Implement role-based access controls so that vendors will only have access to data they need. Businesses can also leverage network segmentation to mitigate the risk of supply chain attacks.
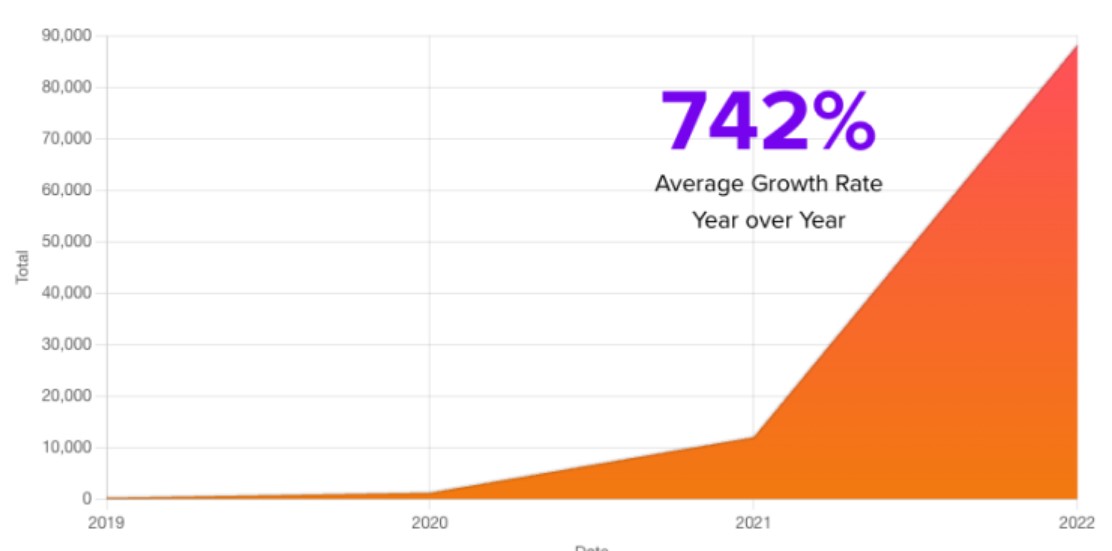
All this helps you limit the access your vendor has so even if they are compromised, the threat actors won’t be able to do much damage to your business. Creating a separate network and limiting the accessibility can drastically restrict the attackers ability to move laterally through the network and do more damage.
2. Reactive Network Defense
Another mistake most businesses make is that they take a reactive approach to cybersecurity in general and network security in particular. This comes back to haunt them as they come to know about intrusion when it is too late or even worse when the damage has been done. To save yourself from getting in such a predicament, it is better to adopt a proactive approach to both cybersecurity and network defense.
This will allow your cybersecurity teams to know about network intrusions when it happens. This gives them more time to react and minimize the damage. The quicker you can identify the intrusion, the better chance you have to minimize the damage as malicious attackers won’t get much time to do the damage.
3. Malicious Actor Collaboration
Gone are the days when cyber criminals used to operate as a small group. Today, they are much more organized and collaborate with one another to launch dangerous cybersecurity attacks. Just like security professionals, who share threat intelligence with one another, cyberattackers can also team up and exchange tools, techniques and intelligence. Ransomware as a service is the best example of this. This makes them more deadly as they can do more damage to businesses. Businesses will also have to get their acts together and work collectively to secure their critical business assets.
4. Ransomware attacks:
Ransomware attacks involve hackers infiltrating a computer system and encrypting the data, demanding a ransom payment in exchange for the decryption key. These attacks can be highly disruptive and costly, and they have been on the rise in recent years. To protect against ransomware attacks, it’s important to regularly update your software and security protocols, and to have a robust backup system in place.
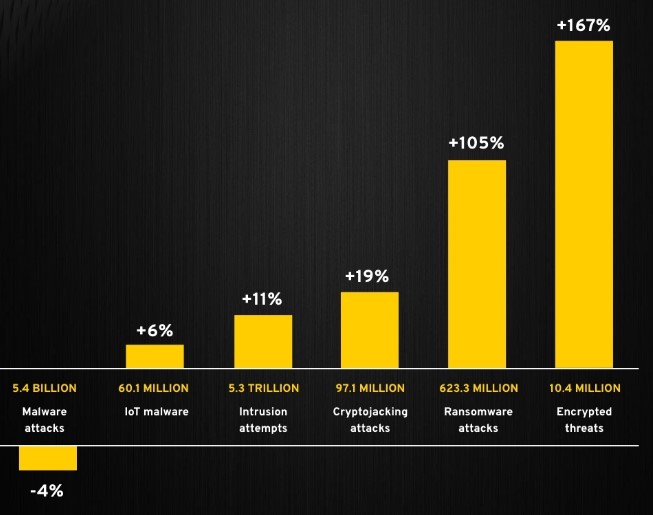
5. Phishing scams:
Phishing scams involve hackers sending fake emails or texts that appear to be from legitimate sources, in an attempt to trick the recipient into divulging sensitive information such as login credentials or financial information. To protect against phishing attacks, it’s important to be suspicious of unsolicited emails or texts, and to verify the authenticity of any requests for sensitive information before responding.
6. Malware:
Malware is software that is designed to harm or exploit a computer system. It can take many forms, including viruses, worms, and Trojans. To protect against different types of malware, it’s important to use antivirus software and to be cautious when downloading files or visiting websites.
7. Man-in-the-middle attacks:
Man-in-the-middle attacks involve hackers intercepting communication between two parties in order to steal sensitive information. These attacks can be particularly dangerous because they often go undetected. To protect against man-in-the-middle attacks, it’s important to use secure communication methods such as encrypted email or virtual private networks (VPNs).
8. SQL injection attacks:
SQL injection attacks involve hackers injecting malicious code into a website’s database in order to gain access to sensitive information. To protect against SQL injection attacks, it’s important to use strong passwords, regularly update your software, and use input validation to prevent malicious code from being injected into your website’s database.
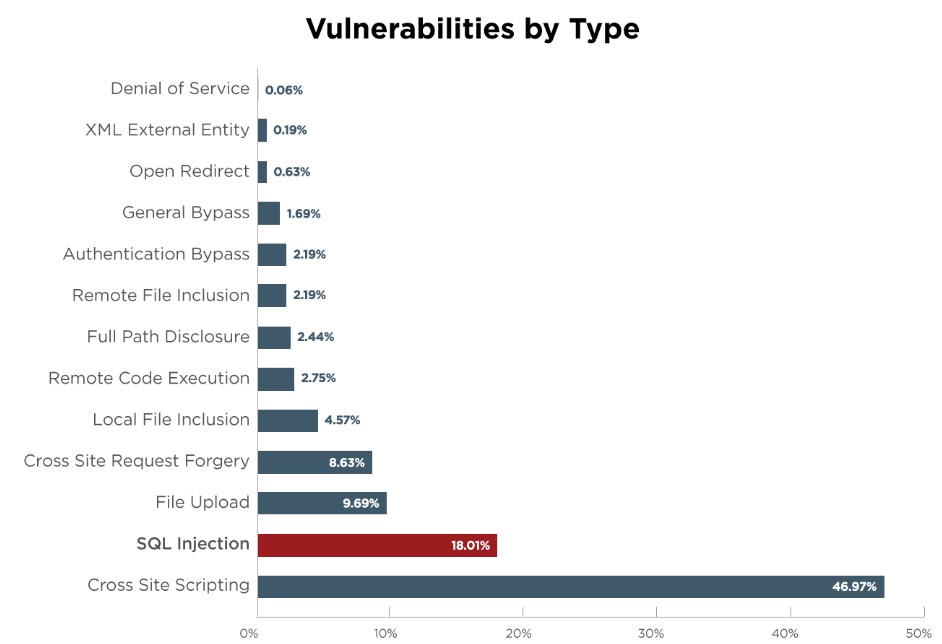
9. Unsecured networks:
Public Wi-Fi networks and unsecured private networks can be vulnerable to hacking attempts. To protect against these risks, it’s important to use secure, encrypted networks whenever possible and to avoid accessing sensitive information on unsecured networks.
10. Insider threats:
Insider threats refer to the risk of employees or contractors intentionally or unintentionally compromising the security of an organization. If you want to save your business from insider threats, it’s important to have robust access controls in place and to educate employees about the importance of cybersecurity.

Conclusion
Cybersecurity risks are an ever-present threat, and it’s important for individuals and businesses to be aware of the latest risks and take steps to protect themselves. By following best practices such as regularly updating software and security protocols, using secure communication methods, and educating employees about cybersecurity, you can help mitigate these risks and protect your sensitive information
Which of these cybersecurity risks poses the biggest risk to your business in 2023? Feel free to share it with us in the comments section below.





Add comment