Vulnerability management is a crucial security practice aimed at preventing potential harm to an organization by continuously identifying, evaluating, and addressing vulnerabilities across its IT ecosystem. With the escalating threat of cyberattacks targeting valuable business information, cybersecurity has become a top priority for organizations.
To combat these threats, businesses are increasingly concentrating on strengthening and fortifying their cybersecurity networks. This article will highlight key vulnerabilities linked to cybersecurity within an organization and their detrimental effects on business operations. Additionally, it will outline an effective methodology for handling vulnerabilities and share insights from customer experiences in implementing this approach.
Vulnerability Management Challenges
Prioritization:
Not all vulnerabilities are equally critical. Determining which vulnerabilities to address first requires a risk-based approach based on potential impact and likelihood of exploitation.
False Positives/Negatives:
One of the biggest issue associated with vulnerability management solutions is that they can give you falst positive and negatives. This means that you coild easily be misled into ignoring a real vulnerability and spending resources on vulnerabilities that are not actually a vulnerability.
Legacy Systems:
Outdated systems and applications may have vulnerabilities for which patches are no longer available. Mitigating these vulnerabilities can be complex.
Complex Environments:
Organizations with a large number of assets and complex IT environments may struggle to identify and manage vulnerabilities across all systems effectively.
Advantages of Vulnerability Management
Early Threat Detection:
Vulnerability management solutions are great at detecting threats early. This gives your cybersecurity teams more time to respond and less time for hackers to do the damage.
Reduced Attack Surface:
By patching and mitigating vulnerabilities, organizations reduce the potential entry points for threat actors.
Informed Decision-Making:
It provides data-driven insights into an organization’s security posture, helping leadership make informed decisions about risk mitigation.
Efficient Resource Allocation:
By optimizing resource allocation, businesses can address high risk vulbnerabilites first as they can post a bigger threat to business continuity.

Vulnerability management is a critical practice for maintaining the security and integrity of IT systems and data.
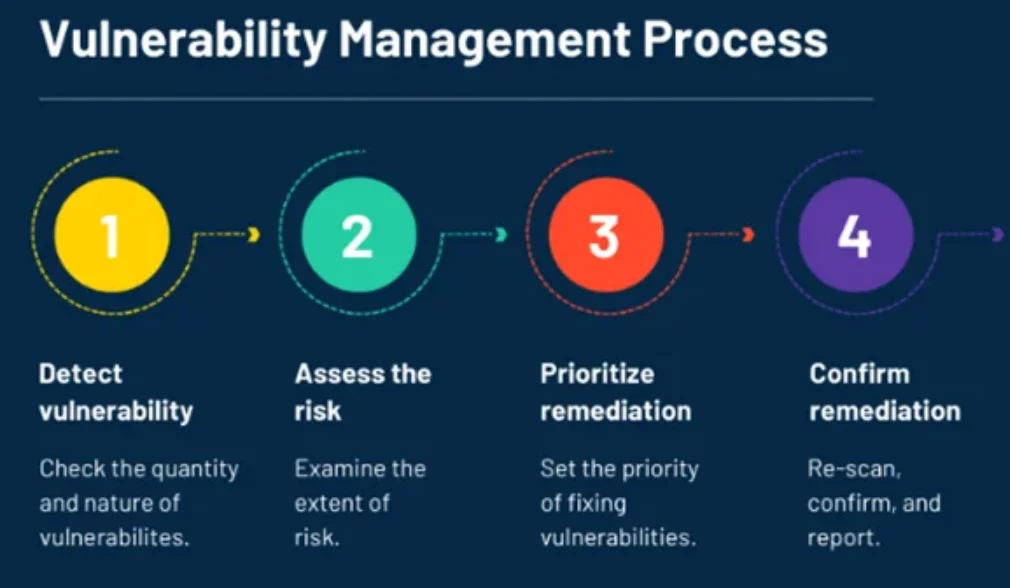
Vulnerability Management Process
Discovery:
Identifying and cataloging assets, systems, and applications within the organization’s environment.
Vulnerability Scanning:
Conducting regular scans to identify vulnerabilities by assessing system configurations, software versions, and potential weaknesses.
Vulnerability Prioritization:
Assigning a risk level to vulnerabilities based on factors such as their potential impact, exploitability, and relevance to the organization’s operations.
Vulnerability Remediation:
Developing and implementing a disaster recovery plan to fix or mitigate identified vulnerabilities. This could involve applying patches, reconfiguring systems, or replacing outdated software.
Validation:
Verifying the effectiveness of remediation efforts through follow-up scans and tests.
Continuous Monitoring:
Regularly monitoring the environment for new vulnerabilities and adapting the strategy accordingly.
Business Impact of Vulnerability Management
In 2018, a social media giant lost over $13 billion in value due to a data breach, which resulted from an exploited vulnerability. Another case in 2013 involved a major retail company losing credit card information of 40 million customers, leading to an $18.5 million loss and reputational damage.
Legal consequences and settlements may arise depending on attack severity. A tech-giant faced multiple breaches in 2014 and 2016, impacting 1 billion user accounts, leading to lawsuits and congressional investigations. Business continuity risks arise as cyberattacks can cause outages, trading disruptions, and system lockouts, as seen in a 2020 incident with a Pacific island stock exchange.
Impact of Vulnerability Management on Threat Modeling Methodologies
Integrating vulnerability management with threat modeling enhances an organization’s ability to address threats comprehensively. Here are some of the ways in which vulnerability management impacts threat modeling methodologies:
Accurate Threat Assessment:
Effective threat modeling requires a realistic understanding of the organization’s vulnerabilities. By maintaining an updated and accurate inventory of vulnerabilities through continuous vulnerability management, threat modeling becomes more precise.
Effective Mitigation Strategies:
Combining vulnerability management with threat modeling empowers organizations to develop tailored mitigation strategies. The insights gained from vulnerability assessments help in crafting targeted and effective countermeasures.
Reduced Attack Surface:
The synergy between vulnerability management and threat modeling contributes to reducing an organization’s attack surface. By proactively addressing vulnerabilities and designing countermeasures, the potential avenues for cyberattacks are minimized.
Adaptation to Dynamic Threats:
The evolving threat landscape demands an adaptive approach to threat modeling. Regular vulnerability assessments enable organizations to adjust their threat models as new vulnerabilities emerge, ensuring that the security strategy remains current.
Conclusion
Vulnerability management stands as a foundational pillar of modern cybersecurity, offering organizations the means to safeguard their digital assets and sensitive information. The integration of vulnerability management with threat modeling methodologies amplifies the effectiveness of both approaches, enabling organizations to identify, assess, and mitigate threats with greater precision and agility. As cyber threats continue to evolve, the collaboration between vulnerability management and threat intelligence becomes even more vital in ensuring robust cybersecurity postures.





Add comment