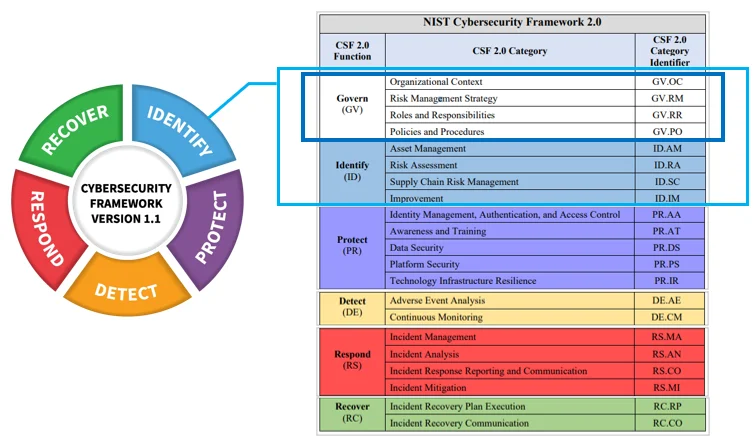
NIST has recently released the next iteration of its cybersecurity framework. This framework adds a sixth function, governance, to the original five, emphasizing cybersecurity as a significant enterprise risk. This move highlights its importance for senior leadership across industries and aims to keep it relevant for diverse organizations, from small businesses to large enterprises, ensuring its accessibility and benefits for current and future cybersecurity needs. By acknowledging cybersecurity as a fundamental enterprise risk, the framework emphasizes its importance in today’s digital landscape.
- NIST Cybersecurity Framework 2.0: A Comprehensive Guide
- How Can NIST Cybersecurity Framework Benefit Your Business?
- Core Elements of NIST Cybersecurity Framework
- Key Changes in Version 2.0 of the Framework
- Using the Framework for Risk-Based Management
- Ongoing Steps for Leveraging the NIST Cybersecurity Framework
- Looking Ahead at the NIST Cybersecurity Framework
NIST Cybersecurity Framework 2.0: A Comprehensive Guide
How Can NIST Cybersecurity Framework Benefit Your Business?
It aims to help organizations:
- Describe their current cybersecurity state
- Define their target cybersecurity state
- Identify and prioritize opportunities for improvement
- Assess progress toward their target state
- Communicate cybersecurity risks with stakeholders
Originally developed through collaboration between government and industry, the framework leverages standards, guidelines, and practices that are already familiar to many organizations internationally.
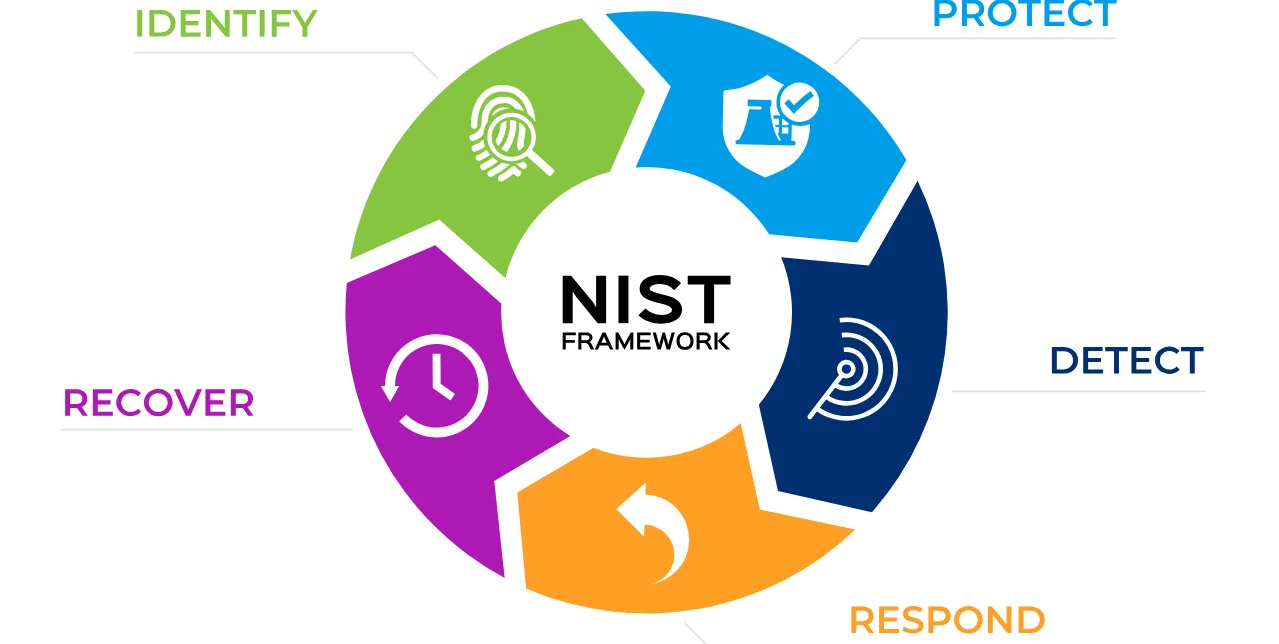
Core Elements of NIST Cybersecurity Framework
The NIST Cybersecurity Framework consists of three main components:
- The Framework Core
- Framework Profiles
- Framework Implementation Tiers
Let’s look at each one in more detail to give you a better idea.
The Framework Core
The Framework Core provides a structured set of cybersecurity activities and desired outcomes that are common across industries and organizations. These are grouped into five concurrent functions:
- Identify – Developing organizational understanding to manage cybersecurity risks
- Protect – Implementing safeguards to ensure the delivery of critical infrastructure services
- Detect – Developing and implementing appropriate activities to identify cybersecurity events
- Respond – Taking action to contain the impact of potential cybersecurity incidents
- Recover – Developing and implementing appropriate activities to maintain plans for resilience and restore capabilities after a cybersecurity incident
For each function, the Framework Core outlines categories and subcategories of cybersecurity outcomes, along with references to globally recognized standards and best practices.
Framework Profiles
Framework Profiles represent the cybersecurity outcomes an organization wants to achieve. Profiles can be used to describe an organization’s current state or its target state. Comparing current and target profiles helps identify gaps to address to reduce cybersecurity risk.
Framework Implementation Tiers
Finally, Framework Implementation Tiers describe how an organization views cybersecurity risk and how they integrate it into their overall risk management practices. The tiers range from Partial (Tier 1) to Adaptive (Tier 4) and help determine the extent to which cybersecurity risk informs organizational strategies and resource allocations.
Key Changes in Version 2.0 of the Framework
- Enhanced guidance on using the framework to evaluate and improve supply chain cybersecurity. With software supply chain attacks on the rise, managing third-party risks is more important than ever.
- Greater emphasis on cyber resilience and ensuring the continuity of critical services in the face of adverse events. The updated framework encourages planning for events like ransomware attacks.
- New sections provide insights into how to establish and mature framework implementation across an organization over time. The framework is presented as more of a living program than a one-time compliance activity.
- Updates to the Framework Core that account for evolving technologies, information, cybersecurity controls, and threats. For example, ransomware is now explicitly called out.
- Alignment with other published standards and guidelines like the NIST Privacy Framework, NICE Cybersecurity Workforce Framework, and ISO standards. This makes the framework part of a holistic organizational approach.
- Removal of separate references to industry sectors. While examples remain, alignment with sector-specific applications is left to related NIST publications like the Cybersecurity Practice Guides.
Using the Framework for Risk-Based Management
A core tenet of the NIST Cybersecurity Framework is taking a risk-based approach to managing cybersecurity. This framework assists organizations in identifying critical assets, evaluating risks related to vulnerabilities and threats, and selecting controls to mitigate cybersecurity risks based on the likelihood of exploitation and potential impact.
To assess risk, organizations should first categorize their systems, assets, data, and capabilities according to criticality. Common criteria include the potential impact should a given asset be compromised or disabled.
Organizations can then conduct risk assessments to identify threats, vulnerabilities, and consequences that could harm critical assets. This helps determine the likelihood and potential impact of cybersecurity events. Conducting recurring assessments allows organizations to adjust evaluations as security threats, vulnerabilities, and business/technology environments evolve.
With risks identified, organizations can create a target profile outlining cybersecurity outcomes that are needed to reduce risks to an acceptable level. The Framework Core’s standards, guidelines, and practices help guide the selection of appropriate security controls and processes. An updated current profile shows progress toward the target.
Ongoing Steps for Leveraging the NIST Cybersecurity Framework
NIST Cybersecurity Framework was designed to complement an organization’s existing cybersecurity program. Its risk-based approach can integrate with and enhance governance, staff training, monitoring, and specific security activities already underway.
Adopting the framework is an ongoing process, not a one-time compliance activity. Organizations should take the following steps to effectively leverage the framework over time:
- Conduct an initial assessment of cybersecurity practices to establish a baseline profile. This can be done through surveys, staff interviews, and policy reviews.
- Build an initial target profile outlining cybersecurity outcomes the organization desires based on their risk assessment and organizational objectives.
- Prioritize and address gaps between the current and target profiles, focusing on quick wins and high-value risk areas. Perform cost-benefit analysis to maximize return on investment.
- Establish metrics based on the framework to monitor cybersecurity progress. Measure the effectiveness of improvements.
- Update current and target profiles regularly as risks and the business environment evolve. Compare updated current profiles against targets.
- Integrate cybersecurity more broadly into enterprise risk management and governance activities leveraging implementation tiers.
- Provide framework awareness training and educational resources to employees to drive cultural adoption.
By taking these steps to ingrain the framework into organizational processes, companies can stay adaptable in the face of emerging cyber threats and vulnerabilities.
Looking Ahead at the NIST Cybersecurity Framework
Since its inception, the NIST Cybersecurity Framework has become arguably the most widely used and authoritative guideline for managing organizational cyber risk globally. Its community of users provides valuable insights that contribute to ongoing framework evolution.
While the cybersecurity landscape will continue to change rapidly, the framework’s fundamental elements are designed to stand the test of time. Its emphasis on assessing and communicating cyber risks provides a foundation for risk-based decision-making that remains highly relevant.
As the cybersecurity challenges facing public and private sector organizations grow, the Cybersecurity Framework will continue to be an indispensable tool. Version 2.0 updates help cement its place as a living resource that can adapt to meet evolving threats and organizational needs. Any organization not currently leveraging the framework should strongly consider its risk-based guidance.
Adoption of frameworks like that provided by NIST is no longer optional. Given the potential impacts of cyber incidents, managing cybersecurity risk has become an essential practice for enterprises. As risks grow, the NIST Cybersecurity Framework will continue providing guidance to keep organizations secure and resilient.





Add comment